Information Technology Reference
In-Depth Information
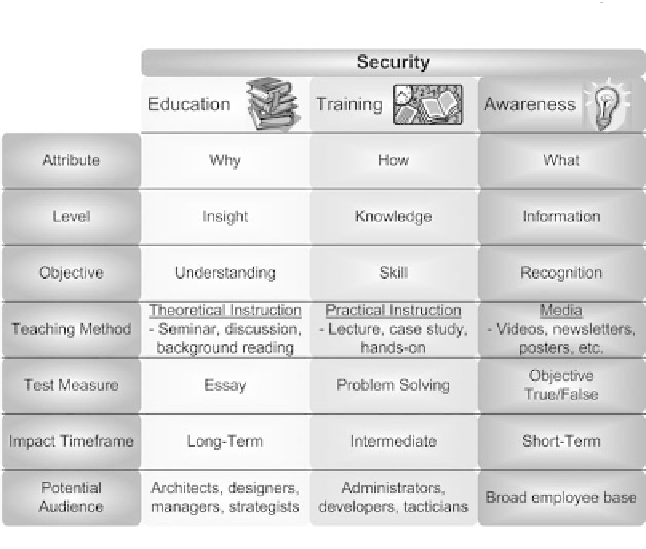
Figure 8.6 SetA comparatie framework. (Deried from niSt Sp800-12.
An
Introduction to Computer Security,
p. 147.)
the program. Many of these answers lie within determining and evaluating the
potential audience.
8.7.1
Security Education, Training, and
Awareness (SETA) Policy
The IA architecture addresses the need for a
SETA policy
. This policy is not so much
concerned with means and method of delivery as it is with specifying a minimum
SETA requirement and providing traceability to business drivers. A SETA policy
specifies new employee induction, including what to cover, a timeframe for deliv-
ery, how to deliver, and various acknowledgments (e.g., sign-off on understanding
and compliance). SETA policy covers similar specifications for ongoing security
awareness and tracking participation and acknowledgment. The policy may also
address the need for visible reminders, such as posters, periodic e-mail, newsletters,
and a permanent intranet site dedicated to security awareness.
Once the SETA policy is developed, the challenge is to create an effective deliv-
ery that promotes understanding and compliance. Architecting a security awareness
program requires identifying and evaluating each potential audience to determine