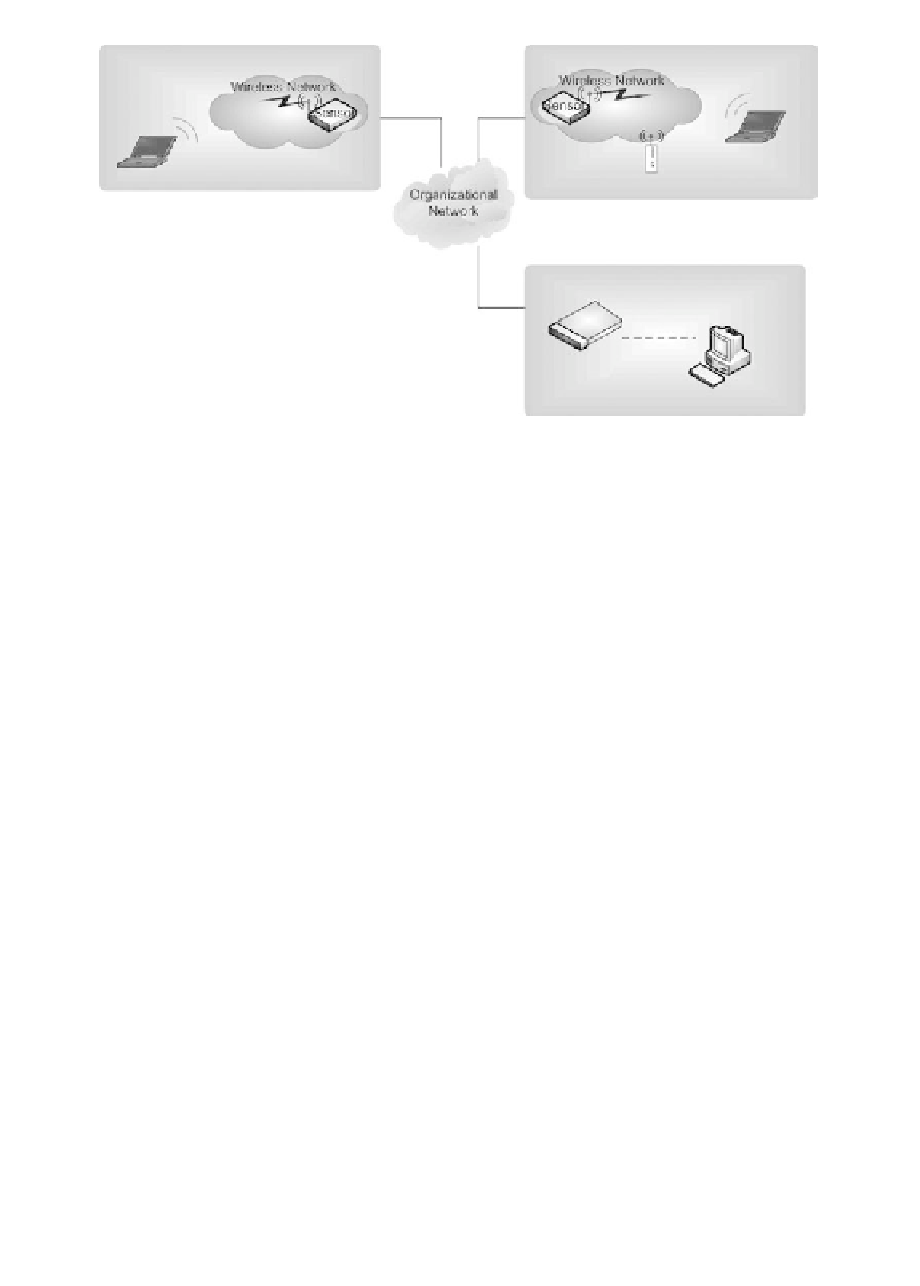
Information Technology Reference
In-Depth Information
Remote Site A
Remote Site B
Accidental
Association
Attacker
Rouge Access Point
Centrally administered, policy-driven distributed
monitoring of wireless networks for attackers,
rouge access points, accidental associations.
Reporting on wireless asset management,
policy violations, and vulnerability assessments.
Central Site
Server
Appliance
Remote Browser
Figure 7.1 Wireless security coniguration oeriew. (the coniguration is
based on AirDefense technology [www.airdefense.net], accessed July 2007.)
n
−
Signal emanation
Strength of signal and direction of signal within building or campus
boundaries
War driving assessments
−
7.4.3.2
Employee Perspective
Provide policy that governs use of wireless technology on PCs and laptops, includ-
ing laptops brought by employees into the work environment. Moreover, provide
security recommendations for home networks that are used to perform work from
home. The additional benefit is to protect any corporate information that may find
itself, intentionally or otherwise, on a home PC. Employee-focused wireless secu-
rity policy considerations include modifying default names and accesses to wireless
routers and wireless LANs, and use WEP or other encryption methods to safeguard
transmissions. Note that using WEP to secure wireless transmissions is like using
a lock on your front door. Both keep out the casually curious, but not a motivated
and prepared adversary.
7.4.4
Practice
For wireless security, practice includes the definition of configuration standards
and procedures; policy drives both of these. One potential wireless security config-
uration is seen in Figure 7.1; the configuration is based on AirDefense technology.