Information Technology Reference
In-Depth Information
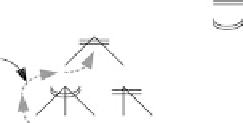
Attack Tree
= And
= Or
T
0
Attack
hread
l
1
l
2
AADR
T0
= Σ ADR
T0,
AADR
l1,
AADR
l2l1
AADR
l2l1
= Σ ADR
l1,
[
> of
{
(ADR
l3,
ADR
l4,
ADR
l5,
)
]
l
3
l
4
l
5
l
6
l
7
Baseline
{
Figure 4.1 Attack defense rating (ADr) metric. (Attack tree nomenclature
inspired by Bruce Schnier's attack modeling.)
tem and the business function which that system supports. Attack modeling pro-
vides a method to examine the potential effect of a threat on a system and on the
business function.
4.3.3
Attack Modeling
:
An example
Defense-in-depth involves many safeguards between a threat and a potential asset
of value. Each physical safeguard (e.g., firewall) may be an interim target on the way
to the asset of value. Each physical device will be a target (T) or intermediate target
(I): T
0
, T
1
, T
i
; I
0
, I
1
, I
j.
Develop an
artificial quantification
for attack difficulty, a
relative scale deriving value from intramodel consistency and consistent application
across the organization. Each entity and entity component is assigned an attack
defense rating (ADR). Additionally, each entity has physical components and logi-
cal components that may be assigned ADR values. Attack modeling separates the
primary service (e.g., firewall) from support services and processes, and separates
primary service vulnerabilities from secondary vulnerabilities (e.g.,
support process
buffer overflow vulnerability).
Lowest-level entities are baseline entities, and all levels above the baseline have
an
aggregate ADR
(AADR) (Figure 4.1). Establish target AADR tolerance param-
eters to evaluate existing defense-in-depth architecture or to model prospective
changes to defense-in-depth architecture. You may also add ADR
weighting
to fur-
ther define relative importance or to reflect risk mitigation.
The ADR model may also represent what-if scenarios, thus providing a
predictive model for new threats and modifications to the defense-in-depth
environment.
4.3.4
IA Quantification: Vulnerability
Vulnerabilities are weaknesses open to exploitation that may damage the organiza-
tion. Vulnerability management is a process identifying vulnerabilities and resolv-
ing or otherwise working around them to minimize the risk of their exploitation
by a threat. Anything in the enterprise may be vulnerable. A vulnerability frame-