Information Technology Reference
In-Depth Information
Limit user access by using user profiles for different departmental roles.
■
Use encryption techniques to secure data or digitally sign data.
■
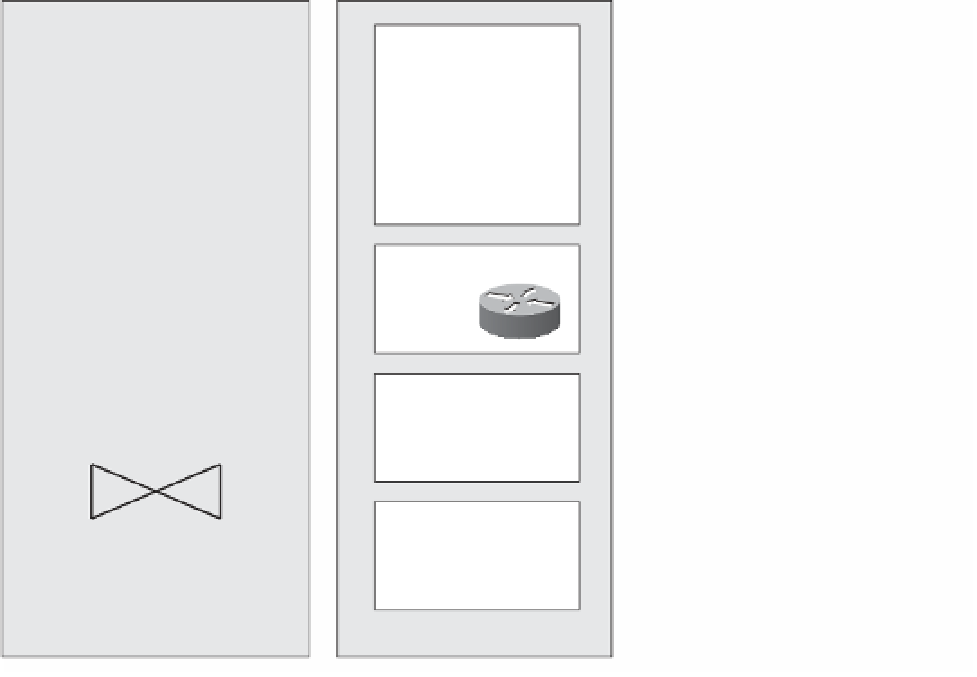
Figure 12-4 shows an attacker viewing, altering, and stealing competitive information. Pay
particular attention to the obstacles the attacker must go through to get to the data.
DMZ/E-Commerce
Enterprise Campus
Building Access
Attacker
Internet
Building Distribution
Internet
Campus Core
View and Alter Confidential
Information
Remote Access VPN
Steal Competitive Information
WAN/MAN
Data Center/Server Farm
Figure 12-4
Confidentiality and Integrity Threats
To p r o v i d e t h e p r o p e r l e v e l s o f s e c u r i t y a n d i n c r e a s e n e t w o r k a v a i l a b i l i t y, a s e c u r i t y p o l i c y
is a crucial element in providing secure network services. This is an important concept to
understand, and such business requirements should be considered throughout the system
life cycle. Business requirements and risk analysis are used in the development of a secu-
rity policy. It is often a balance between ease of access versus the security risk and cost of
implementing the security technology.
In terms of network security in the system life cycle, the business needs are a key area to
consider. Business needs define what the business wants to do with the network.