Information Technology Reference
In-Depth Information
WAN B ackup over the Internet
Another alternative for WAN backup is to use the Internet as the connectivity transport
between sites. However, keep in mind that this type of connection does not support band-
width guarantees. The enterprise also needs to work closely with the ISP to set up the tun-
nels and advertise the company's networks internally so that remote offices have reachable
IP destinations.
Security is of great importance when you rely on the Internet for network connectivity, so
a secure tunnel using IPsec needs to be deployed to protect the data during transport.
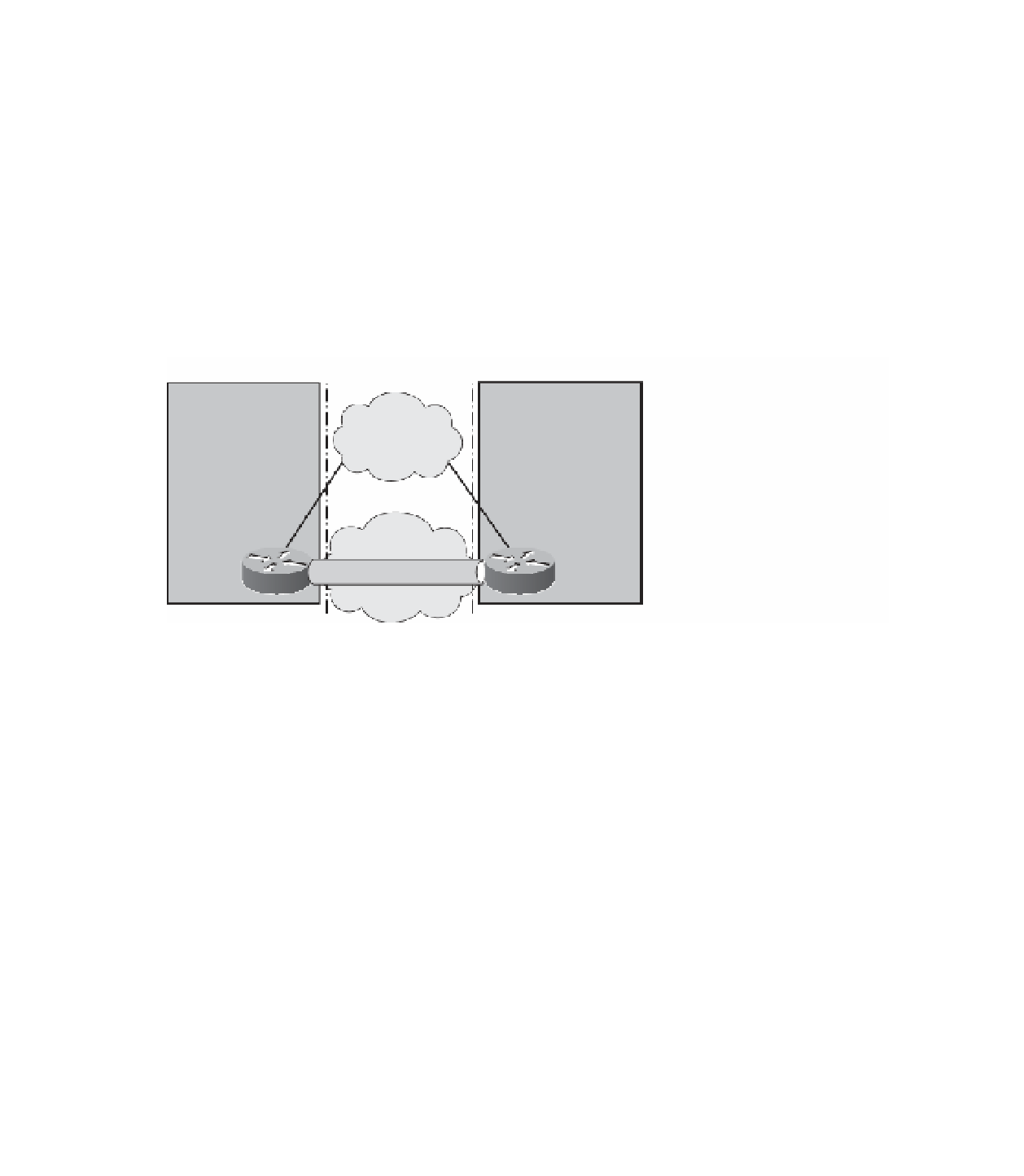
Figure 7-5 illustrates connectivity between the headend or central site and a remote site
using traditional ATM/Frame Relay connections for the primary WAN link. The IPsec tun-
nel is a backup tunnel that provides redundancy for the site if the primary WAN link fails.
Service Provider
Remote Site
Main Office
ATM/FR
WAN
Internet
IPsec Tunnel - Backup
Figure 7-5
WA N B a c k u p o v e r t h e I n t e r n e t
IPsec tunnels are configured between the source and destination routers using tunnel in-
terfaces. Packets that are destined for the tunnel have the standard formatted IP header. IP
packets that are forwarded across the tunnel need an additional GRE/IPsec header placed
on them, as well. As soon as the packets have the required headers, they are placed on the
tunnel with a destination address of the tunnel endpoint. After the packets cross the tun-
nel and arrive on the far end, the GRE/IPsec headers are removed. The packets are then
for warded nor mally u s ing the or ig inal IP packet header s.
When selecting an enterprise WAN architecture, you should identify and understand the
business and technical requirements. It is important to review sample network designs that
could help identify requirements. Here are some common factors that influence decisions
for WAN architec t ure s elec t ion:
High availability:
■
To p i c