Information Technology Reference
In-Depth Information
IPsec endpoints can use static or dynamic IP addressing. Redundancy can be provided at
the headend by using multiple IPsec terminating devices, and each remote IPsec endpoint
can be populated with a list of headend endpoints to make connections with.
IPsec packet payloads can be encrypted, and IPsec receivers can authenticate packet ori-
gins. Internet Key Exchange (IKE) and Public Key Infrastructure (PKI) can also be used
with IPsec. IKE is the protocol used to set up a security association (SA) with IPsec. PKI
is an arrangement that provides for third-party verification of identities.
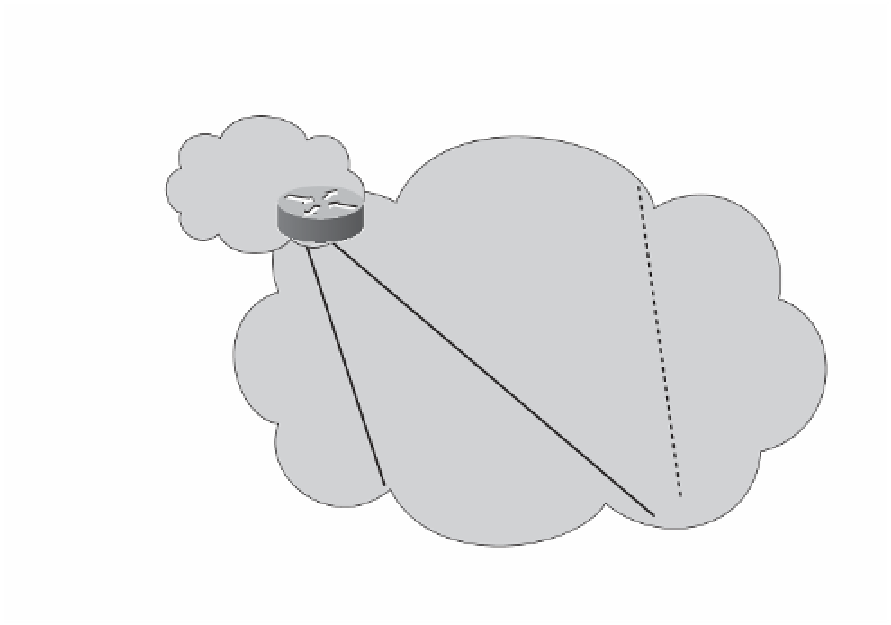
Figure 7-3 shows the topology for IPsec direction encapsulation with multiple headend
sites to provide resiliency for the branch offices.
Headend Site 2
Headend Site 1
Primary IPsec Tunnel
Backup IPsec Tunnel
Branch Site 2
Branch Site 1
Figure 7-3
IPsec Direct Encapsulation Example
Cisco Easy VPN
Although VPNs provide a high level of authentication and encryption of data between
endpoints, it also increases the complexity for the end user to set up and configure. Cisco
Easy VPN remote feature reduces the difficultly inherent with setting up VPN endpoints
by using the Cisco VPN Client protocol. This allows most of the VPN parameters to be
defined at the Cisco Easy VPN Server at the headend site. After the Cisco Easy VPN
Server has been configured, a VPN connection can be set up with a simple configuration
on the Cisco Easy VPN remote. The remote feature is available on the Cisco 800 series
Routers (ISR).