Database Reference
In-Depth Information
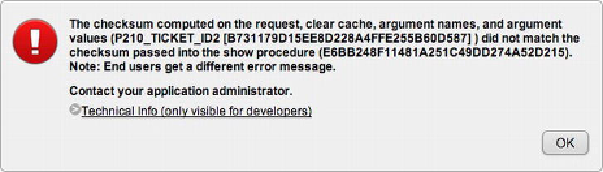
Figure 9-40.
Checksum error message as a result of URL tampering
Summary
In this chapter, you've applied new security to the Help Desk application by utilizing
the key features of APEX. You implemented a new custom authentication scheme to
allow control over users who access the sensitive parts of the application. You also re-
viewed conditional security with both authenticated and un-authenticated individuals
and added parameters to allow the application to be used by both.