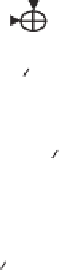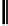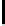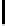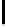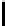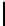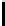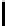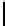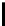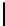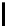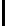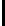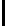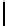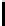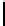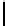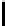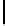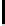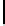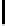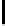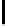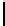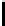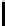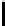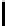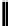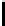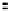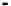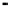Information Technology Reference
In-Depth Information
G
r
A
B
K
r
>>>16
96
(
e
2
)
E
S
32;96
E
E
E
e'
(
e'
)
P
2
X
32;1
96
(
e
1
)
96
(
e
3
)
S
32;96
E
e
= 0 - encryption
e
= 1 - decryption
R =
8
S
32;96
T
r
e'
=
e'
(
e
,
r
);
96
(
e
4
)
E
S
32;96
e
i
=
e
i
(
e
,
r
),
i
= 1,2,3,4
32
Fig. 5.
Encryption round in SCO-1
Ta b l e 2 .
SCO-1: Specification of the switching bits and round subkeys
Round
e
=
0
/
1
e
=
0
e
=
1
e
e
r
K
r
G
r
T
r
e
1
e
2
e
3
e
4
e
1
e
2
e
3
e
4
IT
-
Q
2
Q
1
-
-
-
-
-
-
-
-
-
-
1
Q
1
Q
2
Q
3
1
0
1
0
0
0
0
1
1
0
2
Q
4
Q
1
Q
2
0
1
1
1
1
1
1
1
1
0
3
Q
3
Q
4
Q
1
0
0
0
0
0
0
0
1
0
1
4
Q
2
Q
3
Q
4
1
0
1
1
0
0
0
0
1
0
5
Q
2
Q
4
Q
3
1
1
1
0
1
0
1
0
0
1
6
Q
3
Q
1
Q
4
1
0
0
0
0
1
0
1
0
1
7
Q
4
Q
2
Q
1
0
1
0
1
1
1
1
0
1
0
8
Q
1
Q
3
Q
2
1
1
0
0
1
0
0
0
0
1
FT
-
Q
2
Q
1
-
-
-
-
-
-
-
-
-
-
represented as concate-
nation of four 32-bit subkeys. The key scheduling and specification of the switching bits
are presented in Table 2. The cipher SCO-1 is oriented to cheap hardware implementa-
tion, therefore the SKS was designed in a manner that no reversing the key scheduling
is required to change encryption mode for decryption one. Due to relations
K
r
=
The cipher SCO-1 uses the 128-bit key
Q
=(
Q
1
,
Q
2
,
Q
3
,
Q
4
)
K
9
−
r
,
G
r
=
G
9
−
r
only switching the SCO-box operations is required. Another
interesting peculiarity of this cryptoscheme is the high parallelism of the computations.
Indeed, the operations
S
(
e
1
)
T
9
−
r
,and
T
r
=
32;96
and
S
(
e
2
)
32;96
are performed in parallel and then the operations
S
(
e
3
)
32;96
and
S
(
e
4
)
32;96
are performed also in parallel.
The SCOs can be easily embedded in microcontrollers and general purpose CPUs
and used while designing fast firmware and software encryption systems. Figure 6
shows round functions of the firmware-suitable SCO-based ciphers SCO-2 (a) and