Information Technology Reference
In-Depth Information
b)
a)
S
2;1
S
2;1
S
2;1
S
2;1
V
3
S
2;1
S
2;1
S
2;1
S
2;1
V
1
S
2;1
S
2;1
S
2;1
S
2;1
V
2
V
2
S
2;1
S
2;1
S
2;1
S
2;1
S
2;1
S
2;1
S
2;1
S
2;1
S
2;1
S
2;1
S
2;1
S
2;1
V
1
V
3
1 . . . . . . 8
9 . . . . . . 16
17. . .
. . .24
25. . .
. . .32
c)
d)
V
1
V
2
V
3
V
6
V
5
V
4
S
8;12
S
8;12
S
8;12
S
8;12
I
1
V
4
V
5
V
6
V
3
V
2
V
1
S
-
8;12
S
-
8;12
S
-
8;12
S
-
8;12
25. . .
. . .32
1 . . .
. . . 8
9 . . . . . . 16
17. . .
. . .24
…
…
…
…
x
1
x
64
x
8
x
9
x
16
x
49
f)
e)
…
V
6
V
5
V
4
V
1
V
2
V
3
S
8;12
S
8;12
8
1
2
S
…
…
…
…
8;12
8
1
2
…
I
2
2
8
1
…
V
4
V
5
V
6
-
V
3
V
2
V
1
-
S
8;12
1
2
-
S
1
1
S
1
8
8;12
8;12
…
…
…
…
y
1
y
8
y
9
y
16
y
49
y
64
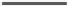
Fig. 3.
Structure of the boxes
S
8;12
(a),
S
−
1
8;12
(b),
S
32;96
(c),
S
−
1
(d),
S
64;192
(e), and
S
−
1
(f)
32;96
64;192
box is a set of 32 parallel
P
(
e
)
2;1
-boxes all of which are controlled with the bit
e
.The
structure of the
S
(
V
,
e
)
64;192
-box is shown in Fig. 4d.
3
Ciphers Based on Switchable Data-Dependent Operations
A number of the hardware-oriented DDP-based ciphers with SKS are presented in [3].
The use of the respective COS boxes instead of the CP boxes in that ciphers leads
to the strengthening the round transformation and possibility to reduce the number of
rounds. However the problem of the weak keys, which is connected with the use of SKS,
remains unsolved. Below we present ciphers SCO-1, SCO-2, and SCO-3 as examples
of the use of the switchable COS boxes in order to avoid weak keys and thwart slide
attacks based on chosen structure of the key. If SKS is used, then the attacker can use
very simple keys and all encryption rounds will define the same substitution providing
homogeneity of the encryption procedure, i.e. prerequisites for some successful slide