Information Technology Reference
In-Depth Information
ABC models for usage control. We further discuss architectural details for usage
control in section 4.
2 Beyond Classical Access Control
One commonality of traditional access controls and even trust management is
utilization of subjects' attributes and objects' attributes for authorization pro-
cess. In other words, in traditional access control, authorization decision is made
based on subject attributes, object attributes, and requested rights. Attributes
include identities, capabilities, or properties of subjects or objects. For example,
in mandatory access control, clearance labels of subjects are considered as sub-
ject attributes and objects' classification labels as object attributes. Authoriza-
tion process, then, evaluates the dominance of these labels along with requested
access rights (e.g., read, write) to return either 'allowed' or 'not-allowed'. Simi-
larly, in discretionary access control, access control list (ACL) can be viewed as
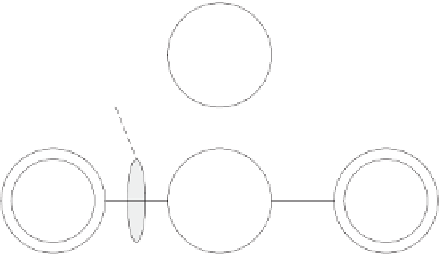
object attributes and capability list as subject attributes. Figure 1 shows this
'attribute-based' traditional access control.
Authoriza-
tions (A)
Usage
Decision
Subjects
(S)
Rights
(R)
Objects
(O)
Subject Attributes
(ATT(S))
Object Attributes
(ATT(O))
Fig. 1.
Traditional Access Control
Although this 'attributed-based' approach of traditional access control can
cover many applications, today's digital information systems require more than
classical authorizations. For example, suppose Alice has to click 'accept' button
for license agreement or has to fill out a certain form to download a company's
whitepaper. In this case, certain actions have to be performed by the subject to
enable a requested usage. In other words, usage decision is based on fulfillment
of required actions, not by existence of subject attributes and object attributes.
This decision factor is called as “obligation” and required in addition to autho-
rization to cover modern access control applications.
In addition to authorization and obligation, there are certain situations where
access or usage needs to be limited due to certain environmental or system