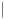Information Technology Reference
In-Depth Information
L
i
R
i
P =(P
L
, P
R
)
IT
L
1
R
1
E
A1,A2
>>> 11
P
32/80
Crypt
A
4
L
2
R
2
E
A3,A4
P
32/80
>>> 17
Crypt
A
3
L
3
R
3
...
G
A3,A4
X
i
L
12
R
12
E
A5,A6
>>> 11
Crypt
P
-1
32/80
R
13
L
13
FT
C =(C
L
, C
R
)
R
i+1
L
i+1
a) Encryption scheme
b) Procedure Crypt
Fig. 4.
(a)Encryption Scheme and (b)Procedure
Crypt
Crypt
is composed of extension box
E
,
CP
-box, non-linear function
G
and
some simple operations (Fig. 4. (b)).
E
extends the 32-bit value to 80-bit control
vector for
P
32
/
80
and
P
−
1
32
/
80
using the subkey
A
1
and
A
2
.
Function
G
is the only non-linear part of SPECTR-H64. It can be illustrated
as follows:
32
, and
X
=
G
A,B
(
W
)
,
where
X, W, A, B
∈{
0
,
1
}
G
:
X
=
M
0
⊕
M
1
⊕
(
M
2
⊗
A
)
⊕
(
M
2
⊗
M
5
⊗
B
)
⊕
(
M
3
⊗
M
5
)
⊕
(
M
4
⊗
B
),
binary vectors
M
0
,M
1
,...M
5
are expressed recursively through
W
as follows:
M
0
=(
m
(0)
1
,m
(0)
2
,...,m
(0)
32
)=(
w
1
,w
2
,...,w
32
) and
∀
j
=1
,...,
5
M
j
=(
m
(
j
)
1
,m
(
j
)
2
,...,m
(
j
)
32
)=(1
,m
(
j−
1)
,m
(
j−
1)
2
,...,m
(
j−
1)
31
).
1
2.3
Key Schedule
Extended encryption key is represented by a sequence of 74
×
32-bit binary
vectors and each round uses 192-bit subkey (
A
1
,A
2
,A
3
,A
4
,A
5
,A
6
). Table. 1
shows the full round subkey structure.
3
Linear Property of SPECTR-H64
In Section 2.1, we mentioned the property of
CP
-box (
P
32
/
80
and
P
−
1
32
/
80
) that
the Hamming weight of input data is equal to that of output data regardless to
the control vector
V
. Let
X
=(
x
1
, ..., x
32
) and
Y
=(
y
1
, ..., y
32
) be the input and