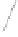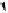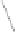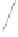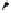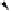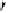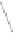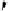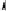Information Technology Reference
In-Depth Information
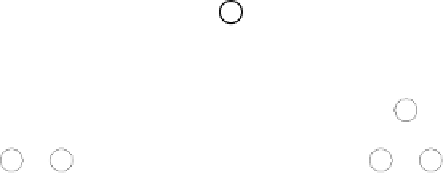
N
3,0
N
2,0
N
Non Adjacent
2,1
LEFT
LEFT
N
1,0
N
1,1
N
1,2
N
N
1,4
1,3
N
0,0
N
0,1
N
0,2
N
0,3
N
0,4
N
0,5
N
0,6
N
0,7
N
0,8
N
0,9
N
0,10
MIDDLE
LEFT
N
3,0
LEFT
MIDDLE
N
2,0
N
Adjacent Nodes
2,1
RIGHT
LEFT
N
1,0
N
1,1
N
1,2
N
N
1,4
1,3
N
0,0
N
0,1
N
0,2
N
0,3
N
0,4
N
0,5
N
0,6
N
0,7
N
0,8
N
0,9
N
0,10
MIDDLE
LEFT
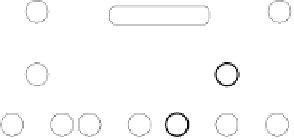
Fig. 6.
Examples of adjacent nodes checking
On the other hand, notice that in some cases minor adjacent, major adjacent
or both are missing. For instance, if
Φ
=
{∅}
, i.e. the MHT is empty, then both
adjacent nodes are missing. If
c
target
<c
j
∀
j
, i.e. the serial number of the target
certificate is smaller than the smallest leaf within the MHT, then there is no
minor adjacent. If
c
target
>c
j
j
, i.e. the serial number of the target is bigger
than the biggest leaf within the MHT, then there is no major adjacent. A serial
number is nothing more than an array of bits and serial numbers with all its bits
set to 0 and serial numbers with all its bits set to 1 are reserved (not assigned to
“real” certificates) to bound the MHT. These “special” serial numbers represent
0 and +
∀
respectively, so that now each possible serial number has two adjacent
nodes independently of the certificates contained by the MHT.
∞
7 Conclusions
In this paper we reviewed the certificate revocation paradigm and the main
approaches to revocation. The authors have developed a revocation system based
on the data structures proposed by Naor and Nissim in their Authenticated
Dictionary called AD-MHT. This paper presents a detailed explanation of a
protocol for the certificate status checking in the AD-MHT. The protocol is a
request/response protocol described in ASN1. In this sense, we also addressed
important aspects associated with the response verification that were beyond
the scope of the original AD specification.
References
1. Aho, A.V., Hopcroft, J.E., and Ullman, J.D.:
Data Structures and Algorithms
.
Addison-Wesley (1988)