Information Technology Reference
In-Depth Information
max=19
min=2
N
2,0
LEFT
MIDDLE
RIGHT
max=5
min=2
max=12
min=7
max=19
min=16
N
1,0
N
1,1
N
1,2
N
0,0
N
0,1
N
0,2
N
0,3
N
0,4
N
0,5
N
0,6
max=2
min=2
max=5
min=5
max=7
min=7
max=8
min=8
max=12
min=12
max=16
min=16
max=19
min=19
LEFT
MIDDLE
LEFT
MIDDLE
RIGHT
LEFT
MIDDLE
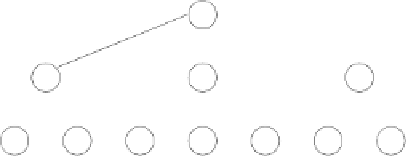
Fig. 3.
Sample 2-3 tree
As mentioned in Section 2, apart from the serial number of the certificate
that has been revoked, the status checking provides the revocation reason and
the revocation date. To add this information to the MHT, we need to include it
in the computation of the cryptographic values of the leaves (5).
H
0
,j
=
h
(
Serial Number
|
Reason
|
Date
)
.
(5)
At the moment, most of the protocols and data structures used in computer
security are defined in ASN1. Below, the authors present a request/response
protocol designed in ASN1 to perform the status checking in the AD-MHT. The
protocol uses definitions from [10] and [4] and can be placed over many transport
mechanisms (HTTP, SMTP, LDAP, etc.).
{
ADMHTRequest ::= SEQUENCE
tbsRequest
ADMHTTBSRequest,
}
optionalSignature
[0] EXPLICIT OCTET STRING OPTIONAL
{
ADMHTTBSRequest ::= SEQUENCE
version
[0] EXPLICIT Version OPTIONAL,
}
requestList
SEQUENCE OF ADMHTCertRequest
{
reqCert
}
ADMHTCertRequest ::= SEQUENCE
CertID
CertID ::= SEQUENCE
{
issuerName [0] EXPLICIT OCTET STRING OPTIONAL,--RDI's DN Hash
issuerKeyHash [1] EXPLICIT OCTET STRING OPTIONAL,--RDI's public key Hash
serialNumber
CertificateSerialNumber
}
CertificateSerialNumber ::= OCTET STRING
Fig. 4.
ASN1 description of the AD-MHT Request
The AD-MHT Request.
Fig. 4 shows the ASN1 description for an AD-MHT request. Each request con-
tains the protocol version (currently version 1), an identifier for each target
certificate and optionally the request might be signed by the client.
Upon receipt of a request, the repository determines if the message is well
formed, if it is configured to provide the requested service and if the request