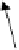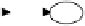Information Technology Reference
In-Depth Information
Conceptually, the detection of a “gene of self-replication” dispersed in a string of
commands is a straightforward task. Analyzing all possible code paths and loops
within the executable code would perform the detection of the self-replication ele-
ment. This technique would function at the source code or machine code level and
would be done prior to its execution. This analysis will be aimed at the establishment
of possible paths and loops within the graph of the code. Figure 1 below illustrates
this problem. It could be seen that the code comprises several paths and a loop con-
taining word “replication”. Many viral codes are available in source code format.
Fig. 1.
Example graph of computer code showing the distributed word “replication”
5.1
Dealing with Encrypted Codes
The analysis of viral code is further complicated if the code is encrypted or encoded.
In many cases, this functionality is normal and expected. For example, self-extracting
compressed archives fall within this category. At execution, the contents of the ar-
chive are decompressed onto some destination media. Since this form of operation, on
its own, is not indicative of viral code, some other technique must be created to actu-
ally “watch” the code during execution. Upon the detection of the self-replicating
element, the executing code should be stopped or frozen until further examination can
be made.
Most modern operating systems were designed under an assumption that none of
the user supplied code can be trusted to execute properly without interfering with
other components of the operating system or other concurrently running applications.
Consequently, a trusted piece of software, the kernel, creates an environment for each
application that is unique and separate from every other application. In order to pre-
vent corruption of the operating system, each application is executed in a lower privi-
lege mode than the kernel. When an application is executed in this reduced privilege
state, it is said to be in user mode. When the kernel is executing, in the higher privi-
lege mode, it is said to be in kernel mode.
For the proper operation of any useful application, there are many operations that
cannot be performed in user mode. For example, most input/output (I/O) operations
require access to physical hardware such as video devices, network cards or disk