Information Technology Reference
In-Depth Information
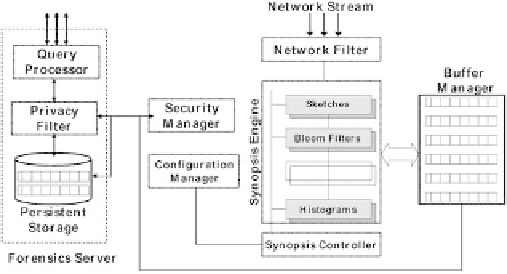
Fig. 2.
Architecture of a SynApp with an Integrated Forensics Server
quirements of an organization). Cheaper SynApps can be designed without per-
sistent storage and query processor. In this case, SynApps periodically send
synopses to the Forensic Server which will handle storage and queries itself. On
the other hand, SynApps can be independent of Forensic Server. In this setup a
SynApp overwrites its old storage whenever it needs more memory and functions
as a self-contained unit sparing the expenses of maintaining a Forensic Server.
We briefly describe the functionality of each element below:
-
Network filter: The appliance may not intend to process every single packet
the router sees and uses the filter to extract useful packets.
-
Synopsis Engine: The engine contains data structures and algorithms that
can be used to represent network tracs succinctly. The data structures
and algorithms can be tuned (for example via a trade-off between space-
eciency and accuracy) via the configuration manager. Each packet that
passes through the network filter is pipelined through the synopsis techniques
implemented in the synopsis engine and each technique decides to process
or not to process a packet based on the signal it receives from the Synopsis
Controller.
-
Synopsis Controller: The Synopsis controller instructs synopsis techniques
in the engine whether to process or not to process a given packet. A rule-set
written by the user and processed by the Configuration Manager allows the
user to modify how packets should be handled by the synopsis engine. Sepa-
rating the design of data structures and algorithms (in the synopsis engine)
and the function of these techniques (how they are mixed and matched, in
the synopsis controller) results in an extensible architecture which can be
programmed to record various events.
-
Configuration Manager: Configuration manager is the interface between a
network administrator and the appliance which allows the administrator to
fine-tune various operations of the appliance.
-
Security Manager: Each query that will be served by the query processor
must be authenticated by the security manager so that rogue queries from
unknown users are simply ignored. In addition, security manager signs and