Information Technology Reference
In-Depth Information
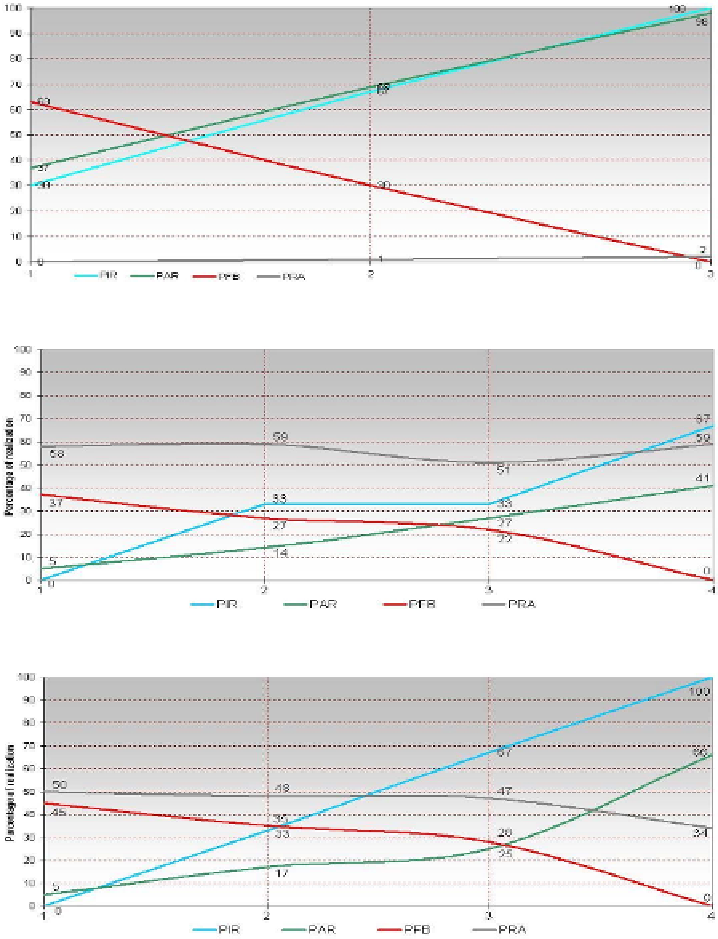
Fig. 4.
Changes of Parameters under Realization of Intention
IS
Fig. 5.
Changes of Parameters under Realization of Intention
GAR
(1)
Fig. 6.
Changes of Parameters under Realization of Intention
GAR
(2)
7
Conclusion
In the paper we described the approach to active vulnerability assessment of computer
networks based on modeling and simulation of attacks and its implementation. The
main peculiarities of the approach
are (1) malefactor's intention-centric and target-