Information Technology Reference
In-Depth Information
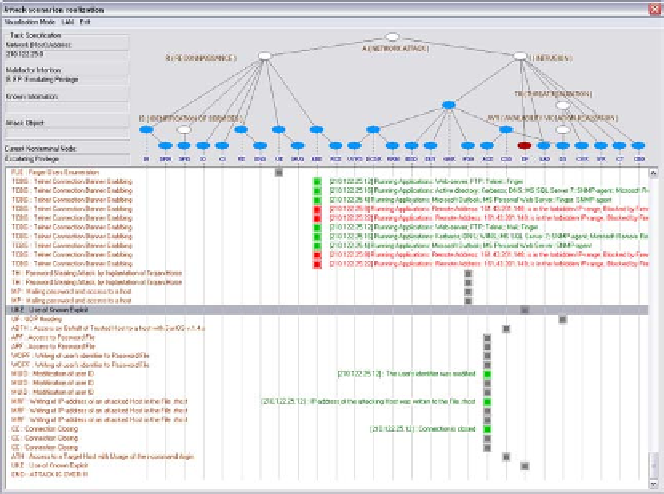
Fig. 3.
Example of Visualization Window of a Network Attack Scenario
4
Case-Study: Examples of Attack Simulation
The main purpose of the experiments conducted with Attack Simulator has consisted
in demonstration of its efficiency for various attacks specifications and attacked net-
work configurations. We have investigated Attack Simulator possibilities for realiza-
tion of two tasks: (1)
checking a computer network security policy at stages of con-
ceptual and logic design of network security system
. This task can be solved by
simulation of attacks at a macro-level and research of responding a network model
being designed; (2)
checking security policy (including vulnerabilities recognition) of
a real-life computer network
. This task can be solved by means of simulation of at-
tacks at a micro-level, i.e. by generating a network traffic corresponding to real activ-
ity of malefactors on realization of various security threats.
Therefore all experiments have been divided into two classes: (1)
Experiments on
simulation of attacks on macro-level
(generation and investigation of malicious ac-
tions against computer network model); (2)
Experiments on simulation of attacks on
micro-level
(generation malicious network traffic against a real computer network).
In the experiments on
simulation of attacks on macro-level
, explorations of attacks
for all malefactor's intentions implemented by Attack Simulator have been carried
out. These experiments were fulfilled under various parameters of the attack task
specification and an attacked computer network configuration. Besides malefactor's
intention, the influence of the following parameters on attacks efficacy was investi-
gated: (1) Protection degree of Network Firewall (PNF); (2) Protection degree of
attacked host (Personal) Firewall (PPF); (3) Protection Parameters of attacked host
(PP); (4) degree of hacker's Knowledge about a Network (KN).