Information Technology Reference
In-Depth Information
iour is not the best place to start with anomaly detection. The detection of anomalies
within the data is a much more promising area of investigation.
SCADA systems are used to control processes ranging from electricity networks to
chemical plants. Although in the longer term a solution is needed that can be applied
to many different areas, it was decided to start with the data from electricity networks,
since this is more systematically related than that from other sources. The techniques
described in this paper are being developed as part of the Safeguard IST project [17],
and they will eventually be incorporated into agents that are used detect and repair
anomalies within large complex critical infrastructures.
2
An Overview of the Electricity Management Network
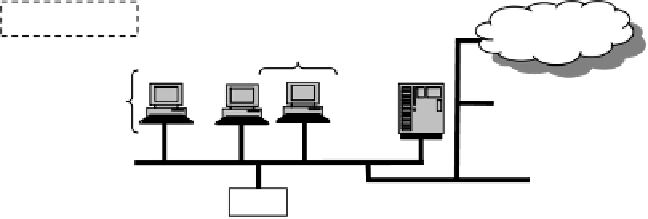
A typical electricity network is managed from a control centre containing a number of
computers running server, database, firewall, monitoring and control software. This is
connected via a wide area network to a number of data acquisition systems (DAS),
which in turn are connected to remote terminal units (RTU), which send data readings
from local sites in response to requests from software running in the control centre.
The electricity network is managed by sending control signals from the control centre
to the RTUs, which control breakers, transformers, switches and so on. The data ac-
quisition and control parts of this management network are its SCADA (Serial Con-
trol And Data Acquisition) system.
Control centre
Manufacturer
support
EMS
system
Operator GUI
PC-based
applications,
including load
management &
state estimation
Independent
System
Operator
Corporate
network
DAS
Data Acquisition System
DAS
DAS
Wide Area
Network
DAS
RTU
RTU
RTU
RTU
RTU
RTU
RTU
RTU
Remote
Terminal Unit
RTU
Fig. 1.
An electricity management network
The data that is gathered by electricity SCADA systems is incomplete and subject
to substantial corruption and loss. To cope with these problems, a program called a
state estimator is used, which takes the data, assigns weights to it according to its
credibility, and uses the known electrical properties of the network to calculate a best-
fit hypothesis about its current state. A limitation of state estimation is that it cannot