Information Technology Reference
In-Depth Information
a generic host process name representing different services currently running, and
therefore can do virtually any operation within the system including access to files,
networks, internet, etc. Upon invocation, svchost interacts with the system in order to
load a file into memory, the algorithm and implementation of such an action is very
similar to the virus described above, however there are some differences:
NtCreateFile 80100080h, {24, 0, 40h, 0, 14678832,
"\??\C:\WINDOWS\Prefetch\CMD.EXE-087B4001.pf""}, 0h,
0, 0h, 1, 96, 0, 0, ... 2080, 0h, 1) result = 0
2
Here the file is opened with the same system call and even the same access mask
(
80100080h
), however the file object does not propagate its handle to any children
processes (flag 40h), nor is it opened with “Read” and “Write” share access flags
(0h). But the main difference in these two system calls is that svchost, being a
legitimate process, does not open itself, instead it is working with other files within
the system.
There is a definite similarity between two processes when it comes to working with
memory objects, which is a normal procedure, and most processes are expected to
have it done in the same manner:
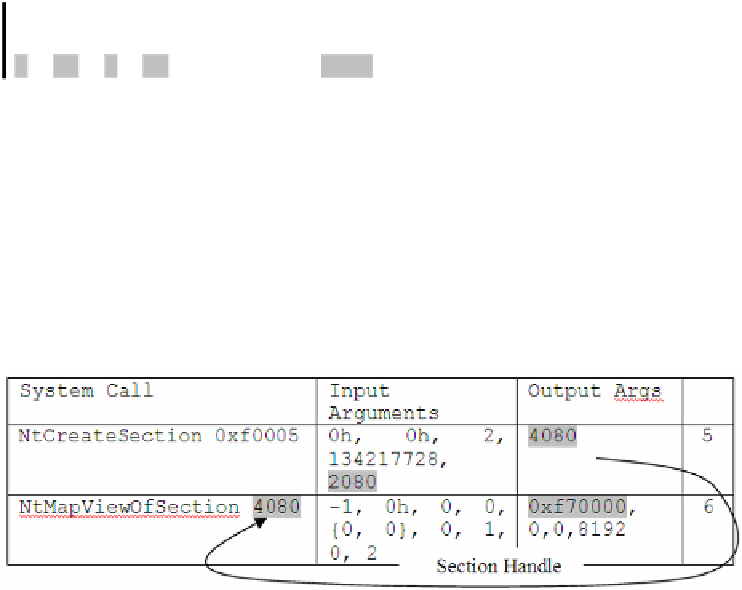
Table 6.
Memory operation in a legitimate program
Therefore, there is a probability for the Memory Mapping Block above to be
detected even in non-malicious programs, but this one block, as well as many other
blocks in
GSR
structure such as Code Injection Block, by itself in no way represents
the entire
GSR
Pyramid.
Finally, the graph below represents the timeline for the legitimate process svchost
as it goes through approximately 240 instructions, many of which in one way or
another relate to some parts of the
GSR
structure. However, process actions never
reach the replication level.
While comparing these two graphs representing two different processes, the
difference in their behavior is obvious. It is expected from a legitimate process to
generate a behavior similar to that of a virus when operating on files and directories,
as they have to use the same API. However the malicious process clearly goes all the
way to the end of the replication procedure on its second attempt, while the legitimate
process, expressing normal behavior, never goes beyond Level 2 no matter how many
“attempts” it makes.