Information Technology Reference
In-Depth Information
5
7-9
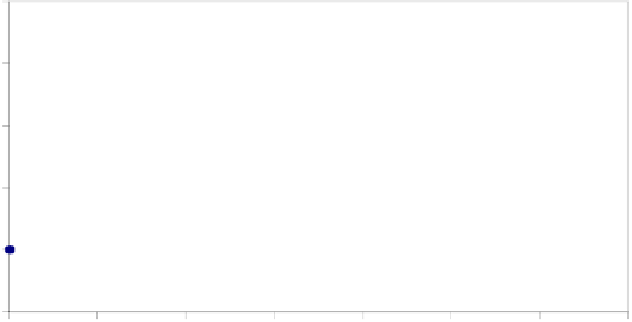
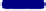
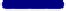
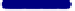
Level 4:
Replication occured
4
Level 3:
Ready for transmission
5
6
5-6
3
Level 2:
Code integration
Attempt # 1
Attempt # 2
4
2
3
3-4
1
Level 1:
Code generation
1
2
2
1
Level 0:
Normal activity
0
0
100
200
300
400
500
600
700
System Call #
Fig. 6.
Sample Virus Replication Data (648 points, 2 attempts)
There are certainly other ways to follow exactly the same algorithm and execute a
successful replication, such as using virtual memory for data swapping instead of the
direct memory access, etc. Also, there are still two more types of replication (see
Table 2) to be covered. There could be many attempts to obfuscate virus code for the
purpose of misleading the detector (i.e. changing object handles on-the-fly before),
however these attempts are easily traceable by the detector since they are also
implemented at a low level with the use of system calls. Finally, the block structure of
the
GSR
allows for detection of many different replication sequences of the same
Gene by simply rearranging building blocks in the
GSR
definition.
5 Parts of Gene of Self Replication in Legitimate Code
While most computer viruses and worms capable of self-replication are believed to be
detectable by their replication activity, there is always a considerable number of non-
viral, fully legitimate pieces of software that have to pass through the monitor
undetected and be able to continue their legitimate actions. After all, the system calls
used to identify the
GSR
are all created to serve these “good” programs. Our major
assumption in this research is that this legitimate software never tries to replicate itself
through any means of communication, either through local disk propagation or remote
network communication. This means that the GSR has to be designed in such a way
that it only incorporates replication blocks from the beginning to the end, as
legitimate code is never supposed to follow replication completely. However, it is
expected, that legitimate software may contain some parts of the
GSR
, and this can
and should be detected in case that the software starts expressing suspicious behavior.
Testing the detector on legitimate processes was a part of the experiment. In this
attempt we were trying to show how close to detection a regular non-infected process
can get. Windows native service process svchost is a good common example of a
regular system process running constantly in the background. This process is actually