Information Technology Reference
In-Depth Information
parameters from its first component, as well as output parameters from its second
component.
In the same manner, after locating a target host file, the virus is expected to open it
and append the viral body to the host so that the control over code execution gets
passed over to the viral code. In our experimental run of the virus, it was able to
locate the “Windows” directory, a very common target for viruses due to a very high
probability of infecting the most important and frequently run system files and
utilities. While searching for a host to infect, the virus invokes another pair of system
calls to locate an executable. This pair forms another replication block called
Host
Search Block
:
Table 3.
Virus searching for executable file in Windows folder
System Call
Input Arguments
Output
Args
NtOpenFile 0x100001 {24, 0, 0x40, 0, 0,
"\??\C:\WINDOWS\""},
3, 16417
12,
{0x0,1}
3
File Extension
NtQueryDirectoryFile
12
0, 0, 0, 1243364,
616, 3, 1, "<.exe", 0
{0x0,110
}
4
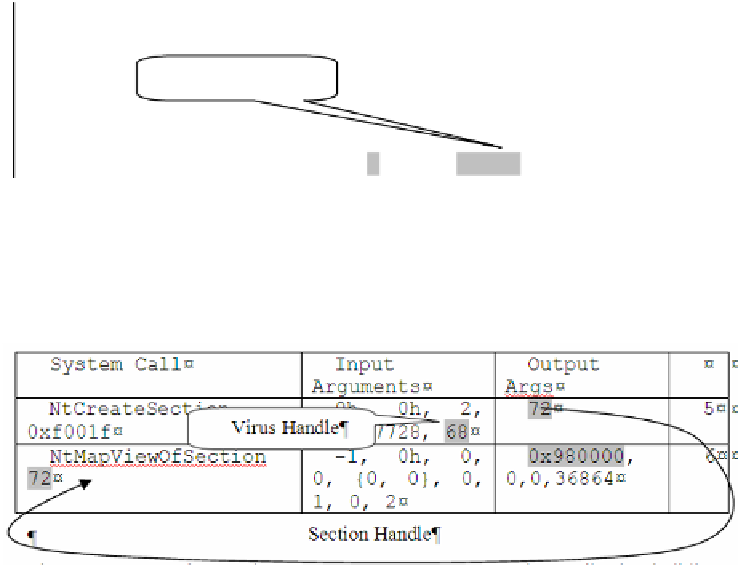
The next step in the replication is to read itself and append itself to the host file.
Since the virus knows perfectly well its own location (output handle # 68 of File
Access Block), it easily executes yet another pair of system calls to map itself into a
memory location 980000h:
Table 4.
Virus maps its body into memory
The memory mapping routine pair allows for defining another replication building
block named
Memory Mapping Block
. Since this block requires a file handle as an
input parameter, which in turn is provided by the File Access Block constructed
earlier, these two blocks are bound into a new higher-level structure named
File-in-
Memory Block
. As usual, the block inherits inputs and outputs of the two parenting
structures.
Finally, when the virus is in memory and the victim file is identified, another set of
system calls is required for completing a successful replication, the set that is
responsible for actually writing the viral code into the host body. However, since
overwriting the host with the virus code would trigger an alarm for to the user, clearly
implying that something is going wrong with the system, it is much more elegant to