Information Technology Reference
In-Depth Information
Interfunctional
Relations
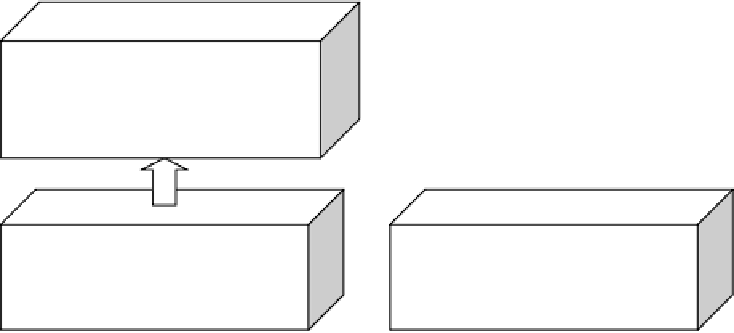
Replication
Block #4
Block #5
Block #1
Block #3
Block #2
Block 1: File Search
Block 2: File Copy
Token set #1
System Calls
Token set#2
System Calls
Arguments
Arguments
ZwQueryDirectoryFile
Handle01,
accessFlag,…
ZwCreateFile
Handle03,
accessFlag,…
ZwOpenFile
Handle02,…
ZwWriteFile
Handle03,…
System Calls
ZwQueryDirectoryFile(…)
ZwOpenFile(…)
System Calls
ZwCreateFile(…)
ZwWriteFile(…)
Fig. 1.
GSP
pyramidal structure
V
V
forms the complete vocabulary
V
(
G
)
=
V
∪
V
The sum of
and
, and
N
N
T
V
V
is indeed an empty set,
V
∩
V
=
Ο
the intersection of
and
.
N
N
T
The set of rules
P
is expressed as
α →
β
β
, where
and
interconnections in
α
V
so that
V
involves at least one simplest block in
.
α
N
S
∈
V
V
Finally,
represents the starting point in
, which corresponds to the
N
N
Gene_of_se
lf_replica
tion
in the structure above.
3.2 Details
In spite of the apparent simplicity of the above structure, in order to accurately
describe the
GSR
the relations between different blocks and system calls could be
very complex. Our research shows that in some cases, the margin between malicious
activity and normal behavior is quite narrow and the differentiation requires fine-
tuning of inter-functional relations.
Normally, a single system call has a unique CID that identifies it to the kernel, a
number of input arguments, a number of output arguments to be generated upon
completion of the system call execution, and the indicator of the result of the