Information Technology Reference
In-Depth Information
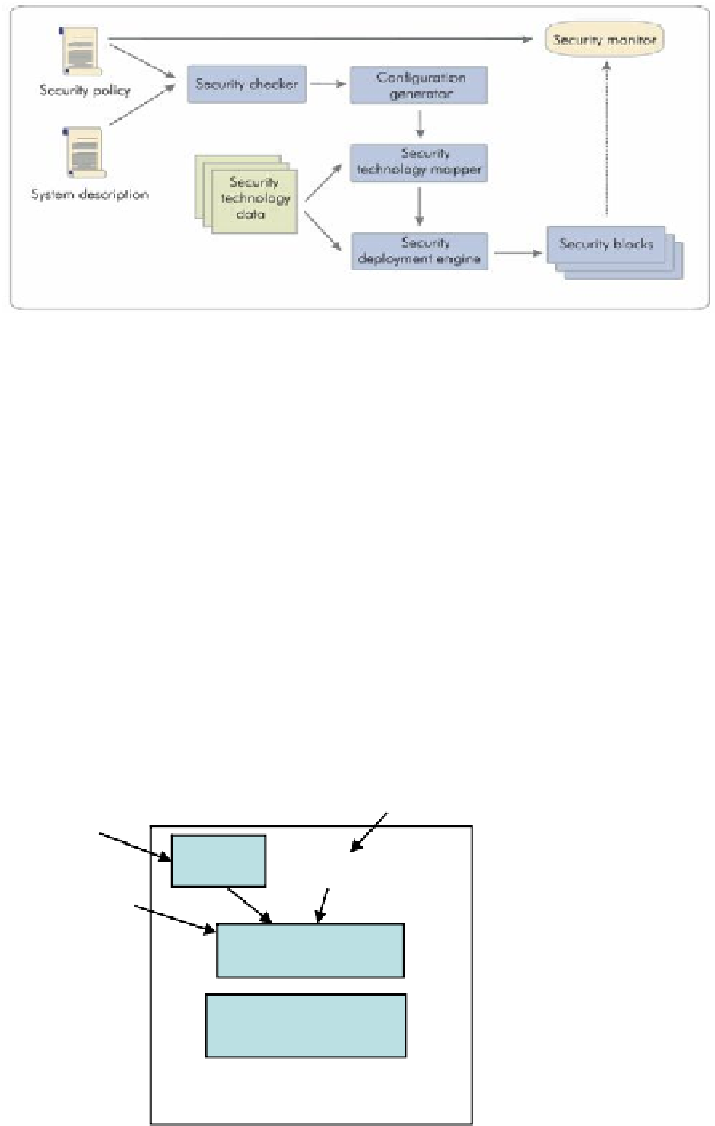
Fig. 1.
General architecture of security policy-based system [10]
the security blocks.
Proactive Security Monitor
(PSM) is an evolution of the concept
of Intrusion Detection System. PSM additionally uses two proactive techniques:
compare network traffic and system behavior against the allowed policy and generate
deliberate attacks to perform automatic checks of the deployed configuration. The
fifth section describes main results and directions of future research.
The SEC architecture is presented in fig. 2. The central box presents SEC, arrows
define dataflow (input or output).
System description (on SDL) is firstly validated using software/hardware
compatibility database. Security policy (on SPL) could be formulated on high or low
level. High-level rule is usually expanded to two or more low level rules for different
security properties, such as authentication, authorization, confidentiality, filtering, etc.
The system stores links between high- and low-level rule formulations. These links
are used to inform system administrator about contradictory high-level rules when
policy conflict is found on low-level. After translation of high-level (HL) rules to
Components
compatibility info
Answer
(GO/NO GO)
SDL
SPL
SEC
HL Rules
validation
!!
Alerts
SDL
validation
HL-LL
translation
rules
“High-level -> Low-
level”
translation
HL - LL rule
interconnection
Descriptions
of conflicts
Verification
(behavior modeling
and conflict resolution)
Info about active / inactive
part of SDL and SPL
specifications
Data for
security
levelevaluatio
Security level evaluator
Security level
Fig. 2.
Security checker architecture