Information Technology Reference
In-Depth Information
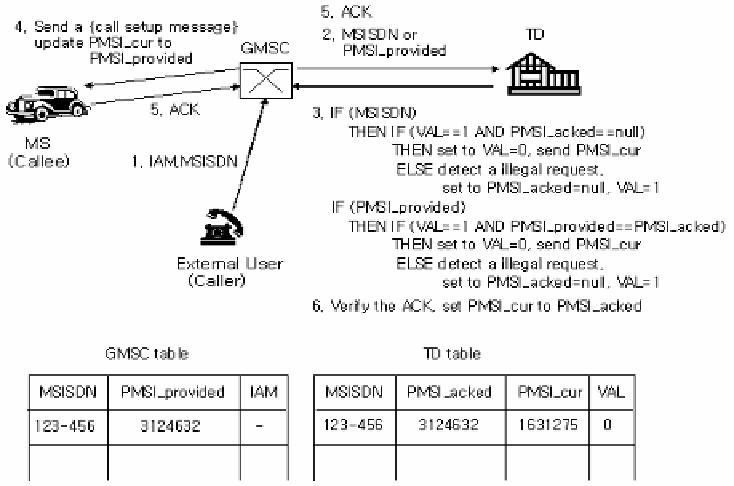
Fig. 1.
Diagram of the request method
Otherwise it sends the value stored in the table to the TD in order to request the
current PMSI.
[Step 3]
the step for notifying the current PMSI after detecting the illegal attempt of
the NP:
(1) In case of receiving the MSISDN, the TD checks the value of VAL in its own
table is 1 at the same time as the fact that the PMSI-acked is null. If the values are 1
and null, the PMSI_cur will be sent to the GMSC after updating the value of VAL to
0. Otherwise, the stored value of the current PMSI_acked and VAL is to be
reinitialized by null and 1 respectively after detecting the illegal attempt, and then
raises an objection through off-line channels.
(2) In case of receiving the PMSI_provided from the GMSC, the TD checks the value
of VAL in its own table is 1 at the same time as the fact that the PMSI_provided is the
same as the PMSI_acked. If the values are 1 and null, the PMSI_cur will be sent to
the GMSC after updating the value of VAL to 0. Otherwise the stored value of the
current PMSI_acked and VAL is to be reinitialized by null and 1 respectively after
detecting the illegal attempt, and then raises an objection through off-line channels.
[Step 4]
the step for the connection setting to the MS:
The GMSC updates the value of PMSI_cur, which is received from the TD, to the
value of PMSI_provided in its own table through the transmission of {call setup
message} to the MS after setting the connection with the external user. There is a
possibility that the PMSI, which is notified by the TD as the connection to the MS
from the side of GMSC, does not exist in its own internal database of HLR and VLR.
Because the MS has already updated in the process as the new value of PMSI or has
not updated as the connection from the GMSC to the MS. Therefore, the GMSC is
able to attempt to connect to the MS by using the updated PMSI with the request of