Information Technology Reference
In-Depth Information
she now has these permissions in the context of the Protection State, Snooping
has occurred because she still does not have an authorized reason (need to know)
to view the file. Finally, if Mallory shares the document with Bob, Distribution
has occurred because Bob has obtained rights to an object he shouldn't have.
This example demonstrates the ability to compartmentalize the problem into
distinct events. This concept will be built on in the next section.
3.3
Model Decomposition
Beginning with each
action
, the threats can be decomposed step by step down to
the leaf nodes. This process is accomplished using a “how it can be performed”
relationship between a parent and child node. The leaf node is the lowest level of
abstraction and depicts the tool the malicious insider has used to accomplish the
activity. A path from the malicious insider (root node) to a tool (leaf node) forms
a completely decomposed activity. The model is developed in an hierarchical
acyclic fashion, meaning a malicious activity can only follow one specific path
from the root node to a leaf node. This indicates that each possible activity is
capable of being explicitly defined.
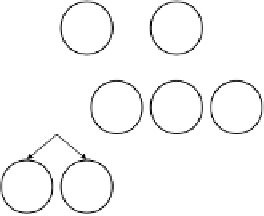
The following is a simple example using this methodology for one Distribu-
tion
action
and is depicted in Fig.2. The Distribution
action
can be performed
through file sharing, which can be accomplished through email, copying the file
to storage media, online chat, or an electronic drop box. The email can be ex-
ecuted through a local account or web based account. In addition, copying the
file to storage can be performed by floppy disk, CD-ROM or USB drive. An
important concept in the configuration is the
actions
are limited to four distinct
possibilities (Distribution, Snooping, Elevation, Alteration). The interim nodes,
however, can use any number of children to expressively describe its parent. This
notion allows for flexibility in the model to tailor it to the policies and specifics
of the individual organization, while still providing an analyzable and decidable
model.
File
Sharing
Copy
To
Media
Electronic
Drop Box
Online
Chat
Email
FTP
to File
Server
Web
Based
Account
Local
Account
Floppy
Disk
USB
Drive
Internet
CD-ROM
Post to
News
Group
Post to
Website
Fig. 2.
An example decomposing the Distribution: file sharing