Information Technology Reference
In-Depth Information
Table 1.
Attack types
Code
Attack type
File 1
File 2
Code
Attack type
File 1
File 2
0
normal
+
+
1
apache2
+
16
pod
+
+
2
back
+
17
portsweep
+
+
3
buffer_overflow
+
+
18
rootkit
+
4
ftp_write
19
saint
+
5
guess_passwd
+
20
satan
+
6
imap
21
sendmail
+
7
ipsweep
+
+
22
smurf
+
8
land
+
23
snmpgetattack
+
9
loadmodule
24
spy
10
multihop
+
25
teardrop
+
11
named
+
26
udpstorm
+
12
neptune
+
27
warezclient
13
nmap
28
warezmaster
14
perl
29
xlock
+
15
phf
+
+
30
xsnoop
+
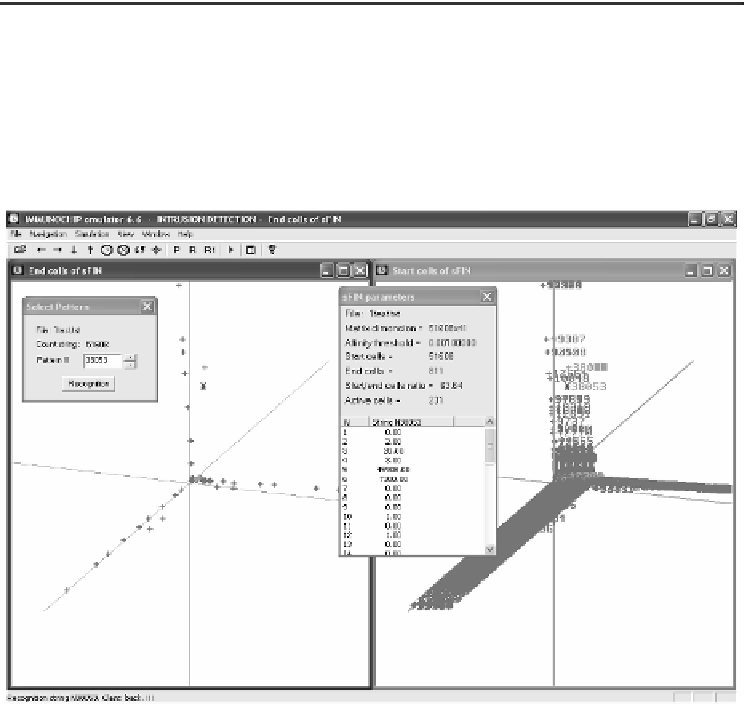
5 Test Results
The results of training the emulator by File 1 are shown in Fig.1, where right-hand
screen represents the initial population of SFIN in 3D space (
3
Z
→ ) after SVD
(start cells = 51608), while left-hand screen shows the population of SFIN after
R
Fig. 1.
Immunochip emulator for intrusion detection