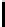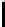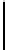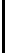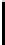Information Technology Reference
In-Depth Information
2.5 Example 1
We now consider an example consisting of four distinct exploits. Each exploit
is represented as a state transition rule. An attacker can chain these together
invariousways(seeFigure1),someofwhich let him penetrate a protected
network. We will use this example in the remainder of this paper to illustrate
and motivate our algorithms and contributions.
DNS Server
δ
1
δ
2
Firewall
(25,53)
H
Attacker
δ
4
,δ
5
DBMS
CS
δ
3
δ
2
Mail Server
Fig. 1.
An example of exploit chaining
Exploits
BIND NXT Remote Root Exploit
The incorrect processing of DNS NXT records by a BIND name server may
allow an attacker to gain a
root
level privilege on a remote vulnerable name
server [3,19]. Let
P
be the primary name server which is authoritative for some
domain, say “foo.com”. The attacker
A
first establishes his machine
H
as the
authoritative name server for some subdomain of “foo.com”, say “bar.foo.com”.
The victim name server
V
is then interactively queried for some host in that
subdomain.
V
then queries
P
which redirects the query to
H
.
H
returns a NXT
record containing exploit code, overflowing
V
's buffer, and spawning a shell for
the attacker. The shell has the same process level that the DNS process had.
Note that the exploit requires that
H
is not running DNS on port 53. We model
the exploit as a rule
δ
1
.
a
1
,a
2
,a
3
,a
4
,a
5
,a
6
,a
7
,a
8
,a
9
;
b
1
δ
1
c
1
;
d
1
where:
a
1
=
sh(A, root, P)
,
a
2
=
sh(A, root, H)
,
a
3
=
reachable(H, V, 53)
,
a
4
=
reachable(V, P, 53)
,
a
5
=
reachable(P, H, 53)
,
a
6
=
service(DNS, 53,
l
1
,
P)
,
a
7
=
service(vul-DNS, 53,
l
2
,V)
,
a
8
=
DNS-authority(P, “foo.com”)
,
a
9
=
DNS-subdomain(P, “bar.foo.com”, H)
,
b
1
=
service(DNS, 53,
l
3
,H)
,
c
1
=
sh(A,
l
2
,V)
,and
d
1
=
service(vul-DNS, 53,
l
2
,V)
.
Generic SSHd Remote Buffer Overflow Exploit
The remote SSHd buffer overflow exploit allows an attacker to get a shell on a
remote host with root privileges. We model this exploit by a transition rule
δ
2