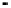Information Technology Reference
In-Depth Information
1
0.7
0.4
k=5
k=15
k=30
0.1
0
0.2
0.4
0.6
0.8
1
False positive rate (%)
Fig. 7.
Performance of the algorithm expressed in ROC curves. False positive rate vs
attack detection rate for
k
=5, 15, and 30
Receiver Operating Characteristic (ROC) is a performance evaluation tech-
nique used to evaluate the intrusion detection algorithm [19]. It is related to the
false error, and it is a trade off between detection rate and false alarms generated
by the intrusion detection system. It can be obtained by varying the detection
threshold and measuring the corresponding number of false alarms. This tech-
nique indicates how detection rate changes affect the raised false alarms. In our
work, we used ROC metric to measure the performance of the proposed algo-
rithm.
To evaluate the proposed algorithm as an anomaly detector, we formed a test
data set from the DARPA BSM data of the 5 days of the sixth training week
(none of the training data was chosen from this week). There are 53 intrusive
sessions included in this testing data, and 14 distinct attacks included in these
intrusive sessions. Also, 10 anomalous behaviors are included, such as unusual
time logging in or from different source logging in, and new commands execution.
Many of the attacks sessions were duplicated and appeared many times, like:
eject
,
neptune
,and
pod
. Duplicated sessions were not considered. Each process
was classified to normal or intrusive, sessions associated with asingleintrusive
process was considered as an attack or anomalous sessions. The performance
of the algorithm is evaluated as the detection rate versus false positive alarms.
Detection rate and false positive alarm were built based on intrusive sessions
detection and normal sessions misclassification. If one session is included in at
least one intrusive process, it is counted as one attack. In our experiments, the
presence of more than one intrusive process in one session does not affect the
number of detection.
The proposed classifier can generate the related large-sequence patterns
L
(
k,l
) of any length of sequences, this length may cover all the elements of
the process, or just part of the process, and it is called the detector window