Information Technology Reference
In-Depth Information
R
PA
R
S
= R
PA
R
S
R
PA
R
S
R
all
R
all
R
all
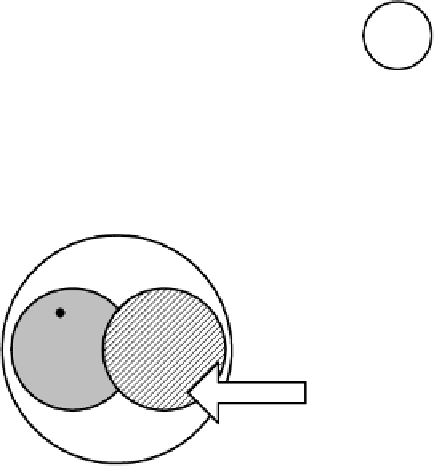
Fig. 4.
Condition P3
Fig. 3.
Condition P2
Fig. 2.
Condition P1
R
all
R
miss
= R
PA
- R
S
R
S
R
PA
R
excess
= R
S
-R
PA
Fig. 5.
Vulnerability Tests in Positive Mode
For negative specification of OSCV-criteria, we have declared another three
conditions of the system security.
Condition N1. Negative Equity.
System is vulnerable (according to the given
criterion), if the set
R
S
of the system-provided rights coincides with the set
R
PD
of the
"denied" rights
, R
S
=R
PD
(fig. 6).
Condition N2. Negative Secrecy.
System is vulnerable (according to the given
criterion), if the set
R
S
of the system-provided rights is not less than the set
R
PD
of the
"denied" rights,
R
PD
⊆
R
S
(fig. 7).
Condition N3. Negative Availability.
System is vulnerable (according to the
given criterion), if the system allows the user to obtain no more than the "denied"
access rights,
R
S
⊆
R
PD
(fig. 8).
To detect the OSCV in negative case, we need to make the following calculus.
R
S
. In this case
R
excess
= R
PD
. The system is vulnerable, for the
current configuration does not denies the "denied" access rights (fig. 9).
Test N1.
R
PD
⊆
, the system is
vulnerable, because the current security configuration does not allow to the user no
one right from the set of the "required" access rights (fig. 9).
Test N2.
R
S
⊆
R
PD
. We have
R
miss
=
R
all
-
R
PD
. If
R
miss
≠
∅