Information Technology Reference
In-Depth Information
Input
is the malefactor's activity,
Output
is the system reaction,
Post-Condition
is a
change of the system state, & is logic connective “AND”. Thus, the module produces
the response of system to attack (for example, after successful attack on scanning
ports the list of open ports is generated) and updates KB about analyzed system (for
example, if a malefactor creates a new user in the group of administrators or starts a
remote administration service, these changes are reflected in KB).
6 Model of Security Level Evaluation
The functionality of the module of security level evaluation is described by a corre-
sponding model which uses a multi-level hierarchy of security metrics.
The taxonomy of security metrics is based on the attack model developed. The
taxonomy contains as the notions of attack realization actions, as well as the notions
of types and categories of assets (secured objects).
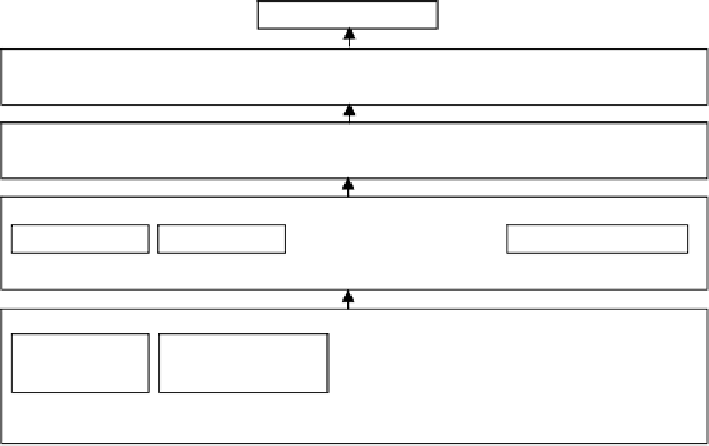
There are four levels of security metrics
sub-taxonomy based on attack realization
actions
(fig.5): (1) an integrated level; (2) a script level; (3) a level of the script
stages; (4) a level of the threat realization. Each higher level contains all metrics of
lower levels (arrow in fig.5 shows the direction of metrics calculation). Examples of
security metrics for this taxonomy are as follows: number of total and successful at-
tack scenarios; number of total and successful stages of attack scenarios; number of
total and successful malefactor attacks on the certain level of taxonomy hierarchy;
number of attacks blocked by existing security facilities; number of discovered and
used vulnerabilities; number of successful scenario implementation steps; number of
different path of successful scenario implementation, etc.
Security Level
Integrated level
Security Metrics Examples: number of total and successful attack scenarios.
Script level
Security Metrics Examples: number of total and successful stages of attack scenarios.
Script stages
…
Reconnaissance
Implantation
Backdoors Creation
Security Metrics Examples: number of total and successful malefactor attacks on each script stage.
Attacks
OS determination
Port scanning
…
Password Guessing
Buffer overflow
…
Security Metrics Examples: Number of discovered and used vulnerabilities;
Number of total and successful malefactor attacks.
Fig. 5.
Security metrics sub-taxonomy based on attack realization actions