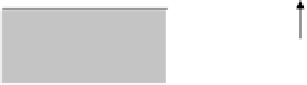Information Technology Reference
In-Depth Information
{
CN
i
} of sub-networks and/or a set {
H
i
} of hosts of the network
CN
;
C
is a set of
connections between the sub-networks (hosts) established as a mapping matrix. Each
host
H
i
is determined as a pair
M
Hi
= <
A, T
>, where
A
is the host address,
T
is a host
type (e.g., firewall, router, host, etc.). The network host resources and functionalities
serve for representing the host characteristics that are important for attack simulation.
These characteristics are represented as follows:
M
Hi
= < A, M, T, N, D, P, S, DP,
ASP, RA, SP, SR, TH,
etc.
>
, where
A
- IP-address,
M
- mask of the network address,
T
- type and version of OS,
N
- users' identifiers (IDs),
D
- domain names,
P
- host
access passwords,
S
- users' security identifiers (SID),
DP
- domain parameters (do-
main, names of hosts in the domain, domain controller, related domains),
ASP
- ac-
tive TCP and UDP ports and services of the hosts,
RA
- running applications,
SP
-
security parameters,
SR
- shared resources,
TH
- trusted hosts.
The implemented algorithm for
module of attack result evaluation
is based on us-
ing a set of rules describing what kind of attacks, in what sort of conditions, and with
what probability (possibility) do have success. The input for these rules is an attack
identifier and a set of parameters defining current state of analyzed system. The out-
put is a probability (possibility) of the attack successfulness.
If system description is sufficiently detailed, then the module of attack result
evaluation can give as a rule univocal answer. But at the design stage the system de-
scription as a rule is incomplete. In this case we need to expand the model of attack
result evaluation with meta-rules, or implement coefficients of probability (possibil-
ity) and evaluate the attack result utilizing these coefficients. For example, the rule
which describes Ping of Death attack: “
IF ATTACK = PoD AND OS_TYPE = Win-
dows_NT AND OS_VERSION = 4.0 AND ICMP_FILTERING = OFF THEN P= 0.8
”,
where
PoD
- an identifier of DoS-attack “Ping of Death”,
P=0.8
means that attack
has success with probability (degree of possibility) 0.8. The OS type, OS version and
the filtering condition are verified using the database about analyzed system.
Response of the information system model on malefactor attacks is a change of its
state and (in some cases) a message directed to attacker (as a system reaction on at-
tack). Each state can be characterized by the attributes describing accessibility of a
system (as a whole one and its certain services), data integrity, data confidentiality,
users and their privileges, etc.
The module of system response generation
fulfills a set
of rules of the system reaction: {
R
SR
j
}, where
R
SR
j
:
Input -> Output & Post-Condition
,
Module of system
response generation
DB of attack signatures
Module of
system
reaction
Network interface
Module of
malefactor actions
recognition
Module of attack
result evaluation
KB about analyzed system (computer network)
Specifications of analyzed system (computer network)
Fig. 4.
Model of analyzed computer network