Information Technology Reference
In-Depth Information
Module of male-
factor's model re-
alization
Module of data and
knowledge reposi-
tory updating
External DB
of threats
and vulner-
abilities
User interface
Module of security
level assessment
Report generation
module
Analyzed
system
Model of
analyzed
system
Module of attack
scenarios generation
Module of scenario
execution
Network
interface
Data and knowledge repository
Design
specifications
DB of attack tools
(exploits)
KB about analyzed system
KB of operation rules
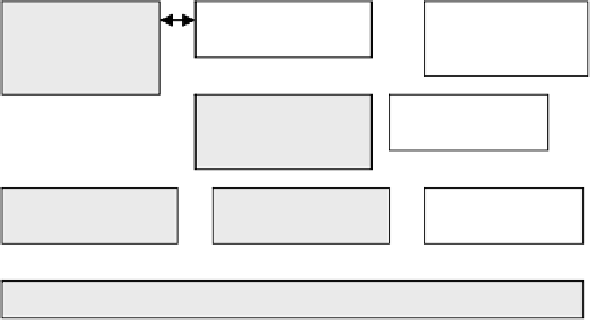
Fig. 1.
Generalized architecture of security analysis system
At the design stage, the SAS operates with the
model of analyzed computer net-
work (system)
. This model is based on design specifications. At the maintenance
stage, the SAS interacts with a real
computer network (system)
.
Let us describe the functions of basic modules.
The module of malefactor's model realization
determines a malefactor's skill
level, a mode of actions and an attack goal.
The data and knowledge repository
consists of a knowledge base (KB) about ana-
lyzed system, a KB of operation (functionality) rules, and a database (DB) of attack
tools (exploits). This repository contains data and knowledge which are as a rule used
by malefactor when he is planning and realizing attacks.
The knowledge base about analyzed system
includes data about the architecture
and particular parameters of computer network (for example, a type and a version of
OS, a list of opened ports, etc) which are needed for scripts generation and attack exe-
cution. This data usually can be received by malefactor using reconnaissance actions
and methods of social engineering.
The knowledge base of operation (functionality) rules
contains meta- and low-
level rules of “IF-THEN” type determining SAS operation on different levels of de-
tail. Meta-level rules define attack scenarios on higher levels. Low level rules specify
attack actions based on external vulnerability database. IF-part of each rule contains
(meta-) action goal and (or) condition parts. The goal is chosen in accordance with a
scenario type, an attack intention and a higher level goal (specified in a meta-rule of
higher level). The condition is compared with the data from database about analyzed
system. THEN-part contains the name of attack action which can be applied and (or)
the link on exploit. An example of one of rules is “
IF GOAL = “Denial of service”
AND OS_TYPE = “Windows_NT” AND OS_VERSION =4 THEN ping_of_death
(PoD)
”. Each rule is marked with an identifier which allows us to determine the
achieved malefactor's goal. For example, the rule mentioned above defines a denial of
service (DoS) attack “ping_of_death”.