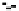Information Technology Reference
In-Depth Information
User Authentication
•
Password/Certificate Mgmt.
•
Public Key Infrastructure
•
Biometric Authentication
•
Smart Cards, Tokens
Data Protection
•
Encryption
•
Opaque Tunneling
•
Watermarking, DRM
•
Data Tagging
•
Tethered Documents
•
Vulnerability Analysis
•
Risk Management
•
Directory
Infrastructure Protection
•
Intrusion Detection (Network, Host, Application, Policies)
•
Firewall, VPN, Intelligent Gateway, Survivable System
•
Pro-active System Health Monitoring, Automated Recovery
•
MLS Servers, Intrusion Response
Fig. 4
Challenges in providing the right mapping from the user to the data
.
small task considering the complexity of authorization logic within this diverse
context and the difficulties of configuring the cumbersome, inflexible, low level
system security mechanisms.
6.2 Consistency, Correctness and Completeness
Consider the following set of hypothetical access control requirements:
•
Mechanical engineers who are citizens have access to privileged engineering
information
•
Interns have no access to any information
•
Any one with access to secret information has access to both privileged and
confidential information
•
Technicians have access to privileged information only if they have clearance
•
CEO cannot be auditor, and vice versa
It is not difficult to see that access control policies are in reality a formal logic model.
•
(
∀
X) (
∀
τ
) (M(X)
∧
C(X)
∧
Π
(
τ
) ⇒ A(X,
τ
))
(1)
•
(
∀
X) (
∀
τ
) (
Ι
(X)
∧
(
Π
(
τ
)
∨
Γ
(
τ
)
∨
Σ
(
τ
)) ⇒
¬
A(X,
τ
))
•
(
∀
X) (
∀
τ
) (S(X)
∧
Σ
(
τ
) ⇒ A(X,
τ
))
•
(
∀
X) (
∀
τ
) (
∀
Z) (
Σ
(
τ
)
∧
A(X,
τ
) ⇒ (
Π
(Z)
∨
Γ
(Z)) ⇒ A(X, Z))