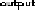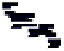Information Technology Reference
In-Depth Information
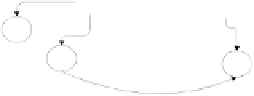
Fig. 3.
SO population process with security knowledge
V.
Present the security requirements to management and security expert(s) for e-
valuation
; if necessary, perform adjustments and/or corrections to security re-
quirements. This step will help towards to the refinement and training of the
information extraction process. The database of security and assurance stan-
dards may be used for enriching the security requirements, in case the informa-
tion contained in the policy documents is deemed insufficient.
3.
Security Actions Definition
VI.
Associate the security requirements with specific security controls;
this step
performs the linking of requirements with deployable security controls (Data-
base of Technical Controls), customized for the concept instance under ques-
tion. In this task, valuable help will be utilized from the infrastructure data col-
lected during step I.
VII.
Transform the controls identified into a Ponder-compatible input;
this step in-
volves the transformation of the controls (actions) specified in step VI into a
form that can be piped into Ponder rules. The Database of Technical Controls
is not a part of Ponder or CIM framework, but rather an enabling repository of