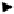Information Technology Reference
In-Depth Information
ASSIGNED ON
Autonomic
Network
Element
BOOT
SOFT BOOT
REFINE
Role
Purpose
ENFORCE
INITIATE
Etiquette
Policy
DEFINE
DEFINE
Fitness
e-rules
Function
Behaviour
Function
CONSUME
PRODUCE
Concern [Workflow] Messages
Community Context
Fig. 6.
Autonomic Node Architecture
A
→
(
+
t
B
)
•
(
1
⁄
c
B
+
d
+
t
A
+
t
C
)
B
C
C
;
(15)
B
→
(
1
⁄
c
B
+
d
+
t
A
+
t
C
)
•
(
d
C
+
t
B
)
A
+
(
1
⁄
d
C
+
c
+
t
B
)
C
C
B
;
C
→
(
1
⁄
d
C
+
c
+
t
B
)
•
(
1
⁄
c
B
+
d
+
t
A
+
t
C
)
B
B
C
,
where
()
i
denotes a residual received from the
i
-th trusted peer. After (15) all
trusted nodes share trusted sub-community state information including weighted node
fitness values (Table 1, last column), and in accordance with the purpose shall try to
increase their fitness and, consequently the fitness of the community. Each node ac-
cording to E4 shall attempt to achieve wider trusted connectivity based on the con-
tents of its message box. In our example only
A
succeeds:
A
that previously was
aware of node
C
(because of
d
()
advertisement) concludes from (15) that its trusted
peer node
B
is in trust with node
C
, it's only possibility to enhance its fitness. Node
A
re-refines its E1 induced etiquette
A
E
1
to advertise to the commu-
→
1
⁄
a
•
(
a
B
+
d
C
)
A
nity the following intended behaviour
A
E
1'
||
||
→
(
1
⁄
a
•
d
C
)
(
1
⁄
c
B
•
1
⁄
b
B
)
(
b
C
•
d
C
)
(16)
A
B
,
where || is the intended concatenation of local behaviours of community members.
Expression (16) is a payload of etiquette message, its concern is yet improved trust in
the community, with message header signalling to community members that node
A
is
proposing certain behaviour. Basically, (16) suggests trusted concatenation of local
workflows: IPv4 forwarding from
A
to
B
, IPv4 to IPv6 interoperability at
B
and IPv6
forwarding from
B
to
C
; reverse IPv6 to IPv4 interoperability at
C
. Though this sam-