Information Technology Reference
In-Depth Information
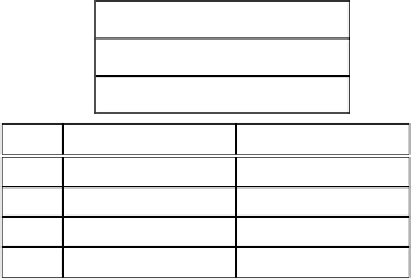
Nodes A, B, C implement the six workflows (WF)
WF(A) = { A.a }
A3
B1
A2
B2
B
WF(B) = { B.a, B.b, B.c }
WF(C) = { C.b, C.d}
A
A1
B5
B3
B4
Name
Workflow
Description
a
F
1,3
IPv4 forwarding
C
IPv4
F
1,4
IPv6 forwarding
b
F
1,3
, F
3,4
, F
1,4
IPv4/IPv6 interop.
C1
c
d
C3
IPv6
C2
IPv6/IPv4 interop.
C1
F
1,4
, F
4,3
, F
1,3
Fig. 3.
Sample communication scenario
Let all the nodes having trust establishment as a common concern to have the fol-
lowing etiquette rules, refined from the purpose of community communication:
• E0: autonomic communication message heard by a node is consumed if message
header represents actual node's concern;
• E1: each active workflow is advertised to the concerned community;
• E2: every heard advertisement of a remote workflow that is locally active is con-
sumed and notified; every consumption notification is consumed (by remote peer);
• E3: the trust per workflow is considered to be established between peers after a
certain number of notifications (
N
n
) is exchanged;
• E4: trust relationships are to be evaluated and progressed in the direction of in-
creasing community fitness.
Consumption of messages is caching and processing of messages per concern. For
the concern of trust the processing of messages is applying the cross operator to each
node's message box; this hides sound behaviours. We extend the notation by overly-
ing consumed message:
a
denotes consumption of
a
and
1
is the notification to the
sender. We reserve to mean:
z
-no trust,
t
— established trust,
x
— trust in progress.
⁄
a
A
FIB
A1
B
B2
Routing
Input
Dgram
Dgram
RC
RC
Auditor
Dgram
Request
NextHop
NextHop
NextHop
Forwarding
Co-work
(
a
)
(
b
)
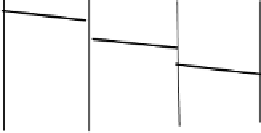
Fig. 4.
Examples of auditing
Etiquette creates prerequisites for auditable trust. Relaying of a micro flow from
Fig. 3 that is presented in Fig. 4 (a) is accompanied by sending back a NextHop