Information Technology Reference
In-Depth Information
E-DHCP Server
E-DHCP Server
Client
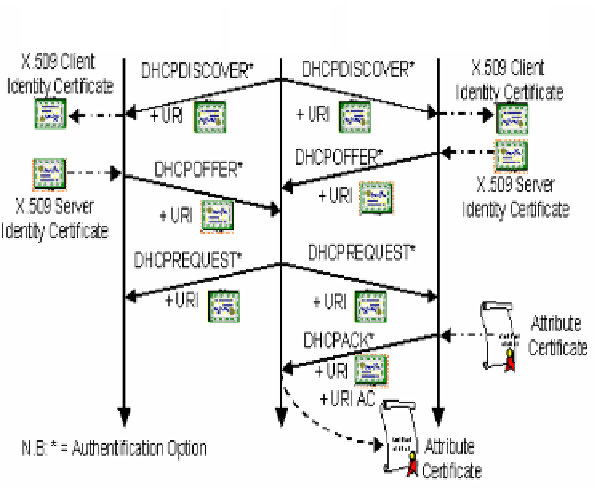
Fig. 3.
E-DHCP Scenario
Information included in X.509 identity certificates will be used by the client and
the server in signature validation for the rest of the transaction. When the server re-
ceives the DHCPRequest message, it will create the client's AC and save it in a data-
base. The server specifies the AC URI in the DHCPACK message. This URI is used
by the client to extract its AC from the database.
4.2 IKE Protocol issue at NAT Environment
4.2.1 IKE Protocol Overview
The Internet Key Exchange Protocol version 1 allows two entities (i.e. network hosts
or gateways) to derive session keys for secure communication via a series of mes-
sages. These exchanges provide authentication and/or encryption for some messages,
and various degrees of protection against flooding, replay, and spoofing attacks.
Currently, the IETF is developing a new version of the IKE protocol that is coming
up in more simplified and efficient way than the existing IKE protocol.
The Internet Key Exchange Protocol version 2 presents a greatly simplified IKE
protocol. IKE v2 is an attempt to simplify the standard, remove the un-needed re-
quirements, and incorporate new standard IPsec functionalities currently contained
within other documents. Unlike IKE v1, which is documented within three separate
documents, IKE v2 is completely described within a single document.
The important difference between IKE v1 and IKE v2 is the reduced number of
round trips required to implement identity protection, the number of possible Phase 1
exchanges is reduced from eight to one. IKE v1 aggressive mode is no longer sup-