Information Technology Reference
In-Depth Information
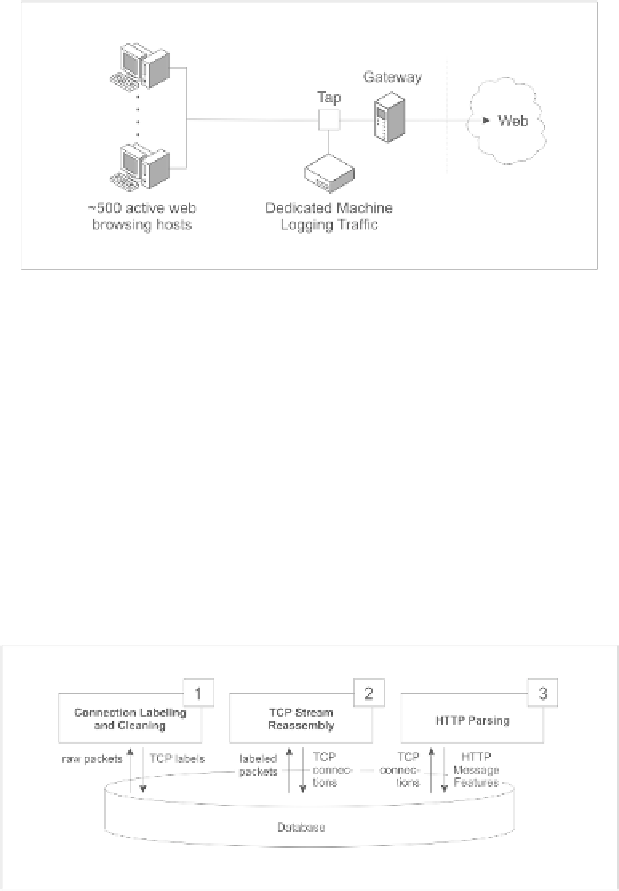
Fig. 6.
Network Under Test
analysis, and logging on IP networks [6]. In this experiment, it was used ex-
clusively for its packet sning and packet logging capabilities. The tool was
configured to break out packets into their constituent fields and write them to
a MySQL [8] database.
Figure 7 shows the three tools used to prepare the data. The first tool labels
all packets by TCP connection and removes broken or empty connections. The
second reconstructs the contents of every TCP connection while preserving the
relationship of those contents with their underlying packet features. The final
tool parses all relevant HTTP features and statistics from each TCP stream.
The results from each of these steps are written back to the database.
Fig. 7.
Three Data Preparation Steps
These tools process the raw packets to produce multiple views of the data
across all relevant protocols. They provide a convenient, granular, and relational
breakdown of every trac feature of interest. All tools were written in C++
and made extensive use of MySQL++ [8], an object oriented API used to access
the database. The API allows queries and query results to be handled as STL
Containers. Shell scripts were used to drive the compiled tools. Perl was employed
for some ancillary tools.