Information Technology Reference
In-Depth Information
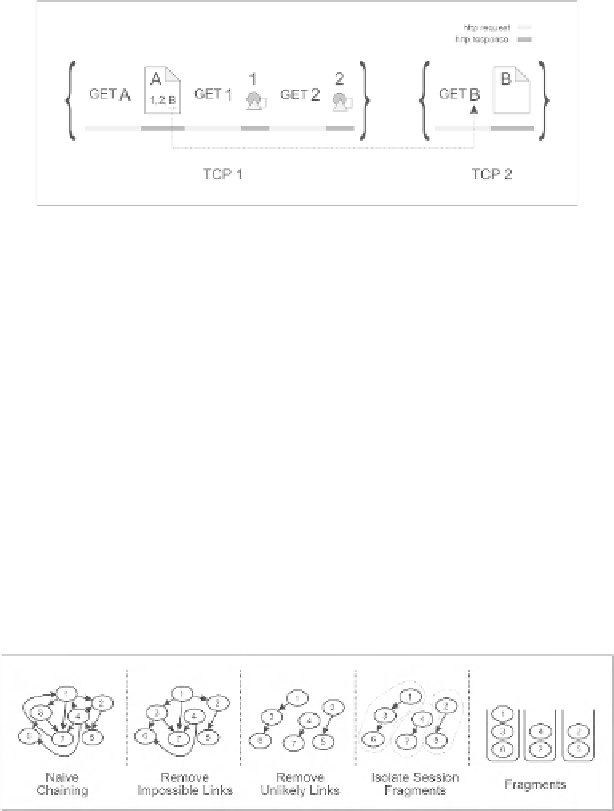
Fig. 1.
Chaining Two Independent TCP Connections
The figure illustrates how the independent connections TCP 1 and TCP 2 can
be chained by matching URLs. The hyperlink B in the first HTTP response of
the first connection is matched with the URL B in the first HTTP request of
the second connection.
The four phases of the Link Chaining technique are: Naive Chaining, Im-
possible Link Removal, Unlikely Link Removal, and Session Fragment Isolation.
The first phase produces a tangled mass of edges and nodes representing all pos-
sible links between all connections. The two subsequent phases chip away at this
mass, selectively removing impossible and unlikely links. By traversing the edges
of the isolated graphs that remain, connection nodes are aggregated into groups.
These groups of connections form session fragments. The process is summarized
in Figure 2.
Fig. 2.
Four Phases of the Link Chaining Attack
The raw inputs to the LCA are reconstructed TCP streams, HTTP messages,
and the HTML hyperlinks they contain. Although these inputs are extracted
from logged packets using known methods, the diculty of this process should
not be discounted. Before links can be extracted from web pages, the pages
must be accurately reconstructed from individual packets. In many cases, the
pages must also be decoded, uncompressed, parsed, and normalized. Relative
links must then be resolved to their absolute form, stored with contextual meta
data like timestamps and connection origin, and indexed appropriately for use
in the LCA. For link extraction to be comprehensive and accurate, the software
must also accomodate imperfect implementations of web protocols. These spec-