Database Reference
In-Depth Information
INTERNET
Applet
Classes
HTML
Class
Loader
Web
Browser
Bytecode
Verifier
Java
Virtual
Machine
Security
Manager
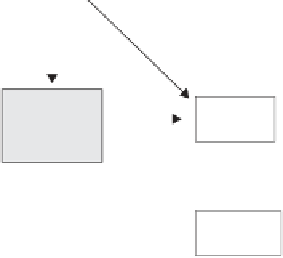
Figure 19-13
Java security.
to be active simultaneously, each with its own namespace. Classes loaded as part of
one applet are not allowed to access other classes, although these can access classes
in standard Java libraries.
Namespaces are organized in a hierarchical manner, allowing JVM to organize
classes based on the origin—local or remote. A class loader does not permit a class
from a less protected namespace to replace a class with a more protected name-
space. Consider the file system's I/O primitives. These are defined in a local Java
class. Therefore, the file system's I/O primitives cannot be invoked or replaced by
classes from outside the local machine.
Bytecode Verifier
The JVM does not allow an applet to run before the bytecode
verifier checks its bytecode completely. The bytecode verifier makes the assumption
that the code is designed to crash the system and intends to violate security. From
this perspective, the bytecode verifier conducts a series of checks, including the exe-
cution of a sophisticated theorem prover to negate its assumption. The theorem
prover ensures that the applet does not forge pointers, bypass access restrictions, or
perform illegal conversion of objects.
Specifically, verification by the bytecode verifier ensures the following:
•
Compiled code is correctly formatted.
•
Internal stacks will not overflow or underflow—traditionally how programmers
breach security.
•
No illegal conversions, such as integer to pointer, will occur.
•
Bytecode instructions are correctly typed.










Search WWH ::

Custom Search