Database Reference
In-Depth Information
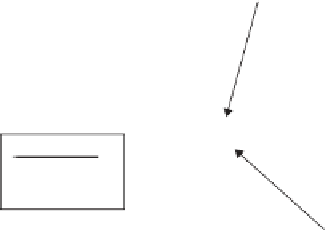
Private Key: 27
Plaintext
Public
Algorithm
SENDER-1
Ciphertext
RECEIVER-1
Ciphertext
Public Keys
Sender-1 19
Receiver-1 13
Plaintext
Private Key: 39
Figure 16-11
RSA: public key encryption.
•
Only an individual user knows his or her private key.
•
The encryption and decryption algorithms are inverses of each other.
Figure 16-11 illustrates this public key encryption technique.
How it Works
Consider the following scenario:
Data provider U1 wants to share data with authorized user U2.
U2 has a public key P2 and a private key R2.
U1 uses the public key P2 of U2 to encrypt the data and transmits the data to U2.
U2 uses the private key R2 to decrypt the data.
If data have to be transmitted securely, it must be extremely difficult for any
intruder to deduce the private key from the publicly known public key and the
encrypting algorithm. The RSA model stands on the premise that it is virtually
impossible to deduce the private keys. This premise rests on the following two facts:
•
A known efficient algorithm exists for testing whether or not a given number,
however large, is a prime number.
•
No known efficient algorithm exists for determining the prime factors of given
number, however large.
Incidentally, one of the authors of the RSA technique had estimated that
testing whether a given 130-digit number is a prime or not would take about
7 minutes on a fast computer. On the other hand, if you have a large number
obtained by multiplying two 63-digit prime numbers, then it would take about
40 quadrillion years on the same machine to determine the prime factors of the
product!
The public key encryption technique treats data as a collection of integers. The
public and private keys are reckoned for an authorized user as follows:




















Search WWH ::

Custom Search