Image Processing Reference
In-Depth Information
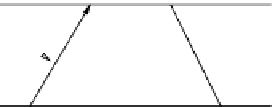
Synchronization pulse
g
2
g
3
B
Acknowledgment
A
g
1
g
4
FIGURE .
Two-way message handshake.
AnothertimesynchronizationtechniquethatadoptssomeconceptsfromNTPisTPSN.heTPSN
requires the root node to synchronize all or part of the nodes in the sensor field. The root node
synchronizes the nodes in a hierarchical way. Before synchronization, the root node constructs the
hierarchy by broadcasting a
level_discovery
packet.heirstlevelofthehierarchyislevel,whichis
where the root node resides. he nodes receiving the
level_discovery
packetfromtherootnodeare
the nodes belonging to level . .Afterwards, the nodes in level broadcast their
level_discovery
packet,
and neighbor nodes receiving the
level_discovery
packet for the first time are the level nodes. his
process continues until all the nodes in the sensor field has a level number.
he root node sends a
time_sync
packet to initialize the time synchronization process. After-
wards, the nodes in level synchronize to level by performing the two-way handshake as shown
in Figure .. This type of handshake is used by the NTP to synchronize the clocks of distributed
computer systems. At the end of the handshake at time
g
,nodeAobtainsthetime
g
,
g
,and
g
from the ACK packet. The time
g
and
g
are obtained from the clock of sensor node B while
g
and
g
are from the node A. After processing the ACK packet, the node A readjusts its clock by the
clock drift value ∆, where ∆
.Atthesametime,thelevelnodesoverhear
this message handshake and wait for a random time before synchronizing with level nodes. This
synchronization process continues until all the nodes in the network are synchronized. Since TPSN
enables time synchronization from one root node, it is type () of the timing techniques.
The TPSN is based on a sender-receiver synchronization model, where the receiver synchronizes
with the time of the sender according to the two-way message handshake as shown in Figure ..
Itistryingtoprovidealightweightandtunabletimesynchronizationservice.Ontheotherhand,it
requires a time server and does not address the robust and energy aware design goal. Since the design
of TPSN is based on a hierarchical methodology similar to NTP, nodes within the hierarchy may
fail and cause nodes to be unsynchronized. In addition, node movements may render the hierarchy
useless, because nodes may move out of their levels. Hence, nodes at level
i
cannot synchronize with
nodes at level
i
=(
g
−
g
)−(
g
−
g
)/
. Afterwards, synchronization may fail throughout the network.
Currently, there is an interest in improving time synchronization schemes and making them
secure from different attacks, such as masquerade, replay, message manipulation, and delay attacks.
One such protocol is HBS [], which is based on TPSN. HBS assumes the cluster heads are high power
sensor nodes that can run encryption algorithms and synchronize using GPS. he cluster heads tag
eachtimingmessagewithasequencenumberandamessageauthenticationcodeusingthesharedkey
between two nodes. he preloaded public/private keys are protected by tamper-resistant hardware.
To authenticate that a timing message sent by a cluster head is valid, neighboring cluster heads
check the message authentication code by using the stored public key. This is assuming that the
broadcast by the cluster head is heard by neighboring cluster heads. If the message authentication
code is not valid, an alarm message will be broadcasted.
Another variation of the TPSN is TSHL [], it has two components, clock skew compensation and
clock offset correction. For clock skew compensation, the beacon nodes send out beacon messages
so nodes can use linear regression to estimate and correct the clock skew. Afterwards, the nodes use
−