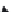what-when-how
In Depth Tutorials and Information
Martryoshka
Intermediate Shells
Figure 10.8
Account and matryoshka creation with key registration for node.
(From Cutillo, L.A., Molva, R., and Strufe, T.
Wireless
On-Demand Network
Systems and Services, 2009.
Sixth International Conference on WONS 2009
.
February2-4,2009,pp.145-152.)
10.3.3.2 Profile Publication
Any data can be classified as public, protected, private data. Public data is signed
by the originator, published by the owner, and replicated at the trusted contacts of
a user on the innermost matryoshka ring. Protected data is managed almost in the
same way as the public data, except it needs to be encrypted by the owner. Private
data is stored by the owner itself and not published. Each node in the system may
dispose three different kinds of data: profile information, trusted contact relations,
and message.
10.3.3.3 Data Retrieval
he lookup of data follows the opposite path compared to the registration. he request-
ing node can access the data based on the respective keys the owner provides.
10.3.3.4 Contact Request and Acceptance
Contact request is sent in the same way as the data request. If the target accepts
the contact relation, it replies by a direct trusted link to
v
and both expand their
inner ring of their matryoshka and executing profile replication and profile
registration.
10.3.3.5 Message Management
Messages are sent in the same way as data retrieval requests. However, they are only
served by the owner of the matryoshka. Besides, the sender signs its message with
its own private node id key and encrypts it for the receiver.