Information Technology Reference
In-Depth Information
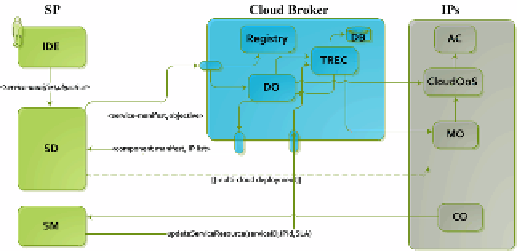
service gets the list of IPs from the
Registry
f)
The
TREC
component of the broker
contains the historical assessments of all SPs and IPs stored in the
DB (Database)
g)
Based on the TREC assessments, the broker filters the IPs and the
DO (Deployment
Optimizer)
initiates SLA negotiations with the filtered IPs
h)
In the process of
negotiation, the broker interacts with the AC(Admission Control) which checks its
current infrastructure status and provides offers based on the request made
i)
Once all
the offers for all the components of the service is received the broker applies the
optimization algorithm to provide the SP with the ranked list of IPs for each of its
service components based on the TREC
j)
The SP deploys all its components
considering the ranked list
k)
The service is deployed using the CO (
Cloud Optimizer
)
at the IP side. The CO provides all VM(
Virtual Machines
) related information to the
SP, which in turn is forward to the Broker
l)
The broker passes the VM information,
to the TREC components to receive monitoring events for these service components
Fig. 3.
High level sequence diagram for broker in OPTIMIS
6
Conclusion and Future Work
In this paper we propose security reputation systems using broker architecture for
cloud service providers, allowing customers to achieve a level of expectation from
cloud service providers about their deployed security systems. By having a broker and
using security reputation based on evidence helps customers build confidence in using
a specific service provider and also gives incentive to cloud providers to demonstrate
their security capabilities to the customers. As future work we intend to identify a
comprehensive security requirements that map to the monitoring infrastructure which
will enable the broker to provide the cloud service provider and the enterprise user
with a generic interface to specify its capabilities and requirements. We also aim to
perform a rigorous evaluation of the proposed architecture by using the simulated as
well as real data of the cloud service providers using the OPTIMIS infrastructure.
Acknowledgment.
This work has been partially supported by the EU within the 7th
Framework Programme under contract ICT-257115-Optimized Infrastructure
Services (OPTIMIS).