Graphics Programs Reference
In-Depth Information
p
active
N
t
request
p
requesting
p
idle
M
t
start
p
accessing
t
end
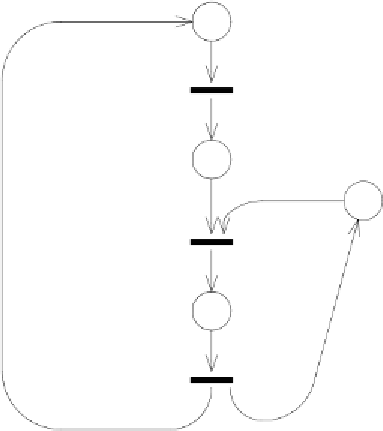
Figure 1.6:
PN description of a system with N users and M resources
in Fig.
1.2(
a). By so doing, the identity of users is lost, and the firing of
transitions corresponds to the change of state of one of the users; which one
is not specified. For example, if N users exist, N tokens may be initially
allocated to place p
active
. The firing of t
request
indicates that one user (which
one is not known) has generated an access request to the resource. The same
can also be done for the resources, if several of them (say M) exist. The
combination of the descriptions then leads to the PN model in Fig.
1.6,
where N tokens are allocated to p
active
, and M to p
idle
(note that the PN
It should be observed that, by taking N = 2 and M = 1, the PN model
that now the user identity is lost. It is interesting to note that this new
model for the case of two users sharing one resource actually corresponds
to a folding of the PN in Fig.
1.5,
where the two user subnets have been
overlaid. The model folding entails a reduction in the number of states of
the model, corresponding to the loss of information about the user identity.
1.2
Fork and Join
Consider next a fork and join behaviour that is typically found in both man-
ufacturing and distributed systems. In its simplest form, such behaviour can






Search WWH ::

Custom Search