Information Technology Reference
In-Depth Information
FIGURE 11.4
Single-firewall layout vs. dual-firewall layout
Perimeter network
(DMZ)
Internal network
(LAN)
Perimeter network
(DMZ)
Internal network
(LAN)
Firewall
Firewall
Firewall
@
@
ISP
ISP
Three-legged with perimeter
network using a single firewall
Network layout with perimeter
network using a dual firewall
The second firewall provides an interface for the internal network, the first firewall (for
outgoing connections), and the perimeter network. This layout is more secure because it
mitigates the chances of the entire network being compromised in the event of an attack.
Security can be further improved if two firewalls are provided by two different vendors
because it makes it less likely that both machines suffer from same security vulnerabilities.
This is commonly referred to as a defense-in-depth security strategy.
Encryption Techniques
To prevent data from unauthenticated use, encryption techniques are widely used for IT
services and products. In the following sections, we cover public key infrastructure, IPSec,
Transport Layer Security (TLS), and a few widely used cipher algorithms.
































































































































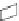



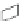







































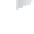






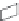
























































































Search WWH ::

Custom Search