Image Processing Reference
In-Depth Information
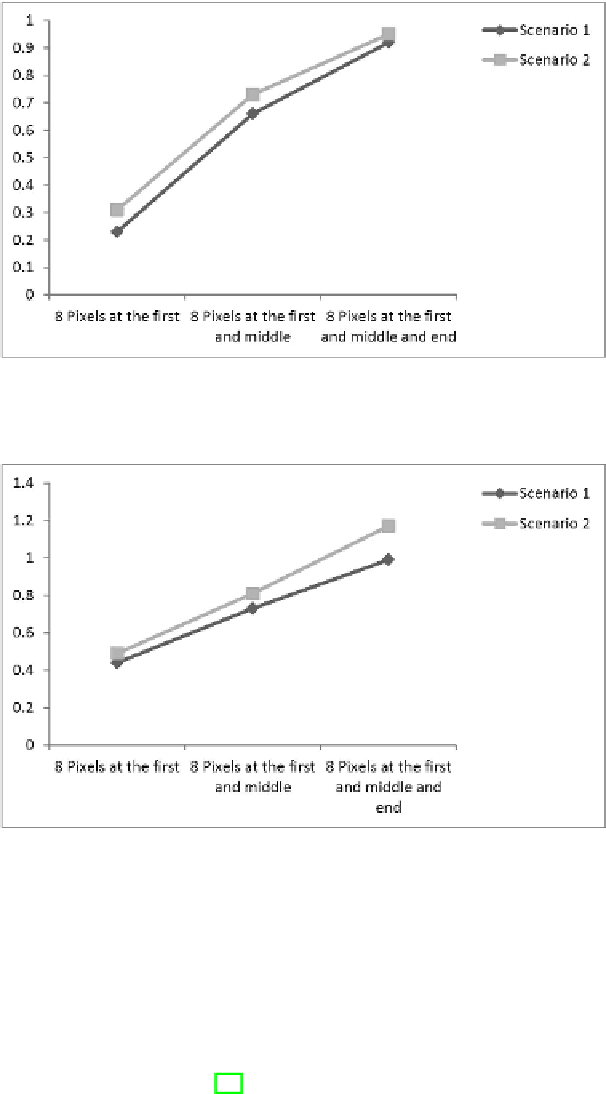
Fig. 7.8
Time consumption for embedding the cipher key into the original image. Here,
we used 50 digital images for each scenario. Vertical axis shows the time consumption in
seconds.
Fig. 7.9
Time consumption for embedding the cipher key into the original image. Here,
we used 100 digital images for each scenario. Vertical axis shows the time consumption in
seconds.
7.4.6
Diffusion
In this experiment the diffusion of our secret key is considered. Diffusion means
that the output bits should depend on the input bits in a very complex way. In a
secret key with good diffusion, if one bit of the plaintext is changed, then the secret
key should change completely [15]. More generally, one may require that flipping a
fixed set of bits should change each output bit with probability one half.
Search WWH ::

Custom Search