Image Processing Reference
In-Depth Information
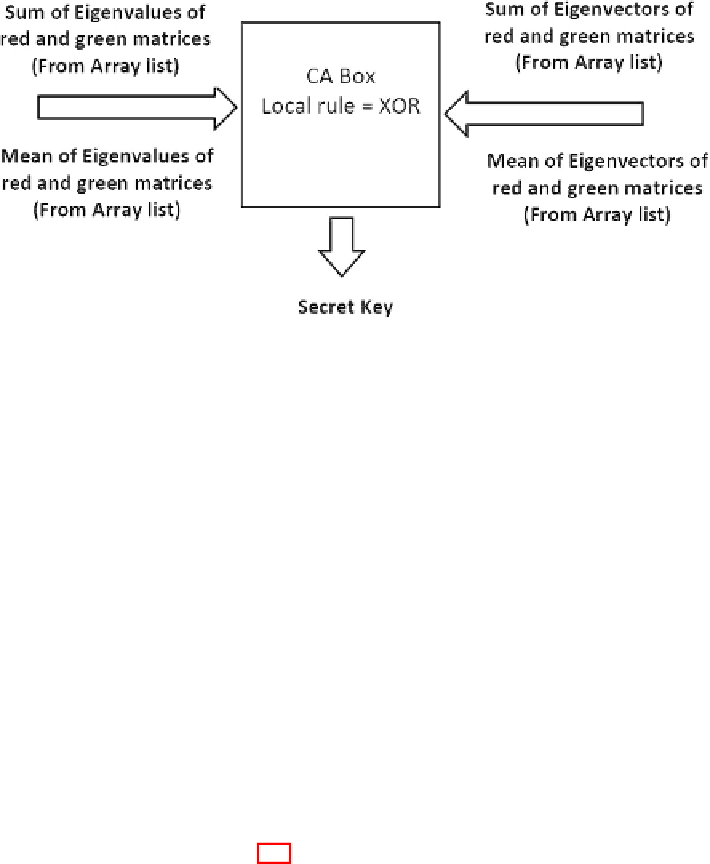
Fig. 7.5
Block diagram of the proposed cellular automata for cipher key creation
To prove the general performance of the proposed forgery detection methods, ex-
tensive experiments using real images were carried out. In particular, a configurable
system has been built to implement both proposed algorithms. This system was built
using JAVA SE with a simple and friendly user interface. All the experiments were
carried out on a 3.00 GHz Intel Dual core 4MB cache with 4GB of RAM running
64-bit Windows 7 operating system. Seven experiments will be presented in this
section to show the implementation and the results of the proposed methods. These
are as follows:
• Performance and visual quality
• Time consumption
• True and False Alert
• PSNR
• Cipher key sensitivity
•D fu ion
•
Comparison with non-CA works
In order to evaluate the above aspects of our proposed method, we perform sev-
eral tests on the dataset (Table 7.5).
7.4.1
Performance and Visual Quality
Figure 7.6 shows the original images and data embedded output .png images which
generated via scenario 1 to prove the performance and visual quality of the proposed
method. By considering same images, input and output images using scenario 2 are
shown in Figure 7.7.

Search WWH ::

Custom Search