Information Technology Reference
In-Depth Information
(a)
(b)
(c)
Fig. 2.
Parse trees of output pages for the running example. Trees (a) and (b) represent
safe executions. Tree (c) represents an injection attack.
classes of possible variations. Under these assumptions, the security oracle prob-
lem can be formulated as a binary classification problem, that can be addressed
by relying on kernel methods. In particular, we deal with parse trees, so kernel
methods that fit this problem definition better are
tree kernels
[5].
In constructing the oracle, first we need to run static analysis to get a list of
potential vulnerabilities in a preparation step:
















































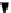




Search WWH ::

Custom Search