Information Technology Reference
In-Depth Information
Fig. 5.
Result of the weaving
In Fig. 1, the cSD
log in
represents a customer log in on a server. The customer
tries to log in and either he succeeds, or he fails. In this last case, the customer
can try again to log in, and either he succeeds, or the server answers “no”. The
expected weaving of the three aspects depicted in Fig. 4 into the cSD
log in
is
represented by the cSD in Fig. 5.
3
Various Definitions of Join Points
As mentioned in the introduction, weaving multiple aspects at the same join
point can be dicult if a join point is simply defined as a strict sequence of
messages, because aspects previously woven might have inserted messages in
between. In this case, the only way to support multiple static weaving is to define
each aspect in function of the other aspects, which is clearly not acceptable.
The weaving of the three aspects depicted in Fig. 4 allows us to better explain
the problem. If the join points are defined as the strict sequence of messages cor-
responding to those specified in the pointcut, the weaving of these three aspects is
impossible. Indeed, when the aspect
security
is woven, a message
save bad attempt
is added between the two messages
. Since the pointcut detects
only a strict sequence of messages, after the weaving of the aspect
log in
and
try again
security
,theas-
pect
display
cannot be woven anymore. We obtain the same problem if we weave
the aspect
afterwards.
To solve this problem of multiple weaving, we introduce new formal defini-
tions of join points which make possible the detection of join points where some
events can occur between the events specified in the pointcut. In this way, when
the aspect
display
first and the aspect
security
security
is woven, the pointcut of the aspect
display
will allow the
detection of the join point formed by the messages
log in
and
try again
,evenif
the message
save bad attempt
has been added.












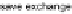






































Search WWH ::

Custom Search